
by Gary Mintchell | Mar 20, 2018 | Automation, Data Management, Internet of Things, Operations Management
Much of the interesting activity in the Industrial Internet of Things (IIoT) space lately happens at the edge of the network. IT companies such as Dell Technologies and Hewlett Packard Enterprise have built upon their core technologies to develop powerful edge computing devices. Recently Bedrock Automation and Opto 22 on the OT side have also built interesting edge devices.
I’ve long maintained that all this technology—from intelligent sensing to cloud databases—means little without ways to make sense of the data. One company I rarely hear from is FogHorn Systems. This developer of edge intelligence software has recently been quite active on the partnership front. One announcement regards Wind River and the other Google.
FogHorn and Wind River (an Intel company) have teamed to integrate FogHorn’s Lightning edge analytics and machine learning platform with Wind River’s software, including Wind River Helix Device Cloud, Wind River Titanium Control, and Wind River Linux. This offering is said to accelerate harnessing the power of IIoT data. Specifically, FogHorn enables organizations to place data analytics and machine learning as close to the data source as possible; Wind River provides the technology to support manageability of edge devices across their lifecycle, virtualization for workload consolidation, and software portability via containerization.
“Wind River’s collaboration with FogHorn will solve two big challenges in Industrial IoT today, getting analytics and machine learning close to the devices generating the data, and managing thousands to hundreds of thousands of endpoints across their product lifecycle,” said Michael Krutz, Chief Product Officer at Wind River. “We’re very excited about this integrated solution, and the significant value it will deliver to our joint customers globally.”
FogHorn’s Lightning product portfolio embeds edge intelligence directly into small-footprint IoT devices. By enabling data processing at or near the source of sensor data, FogHorn eliminates the need to send terabytes of data to the cloud for processing.
“Large organizations with complex, multi-site IoT deployments are faced with the challenge of not only pushing advanced analytics and machine learning close to the source of the data, but also the provisioning and maintenance of a high volume and variety of edge devices,” said Kevin Duffy, VP of Business Development at FogHorn. “FogHorn and Wind River together deliver the industry’s most comprehensive solution to addressing both sides of this complex IoT device equation.”
Meanwhile, FogHorn Systems also announced a collaboration with Google Cloud IoT Core to simplify the deployment and maximize the business impact of Industrial IoT (IIoT) applications.
The companies have teamed up to integrate Lightning edge analytics and machine learning platform with Cloud IoT Core.
“Cloud IoT Core simply and securely brings the power of Google Cloud’s world-class data infrastructure capabilities to the IIoT market,” said Antony Passemard, Head of IoT Product Management at Google Cloud. “By combining industry-leading edge intelligence from FogHorn, we’ve created a fully-integrated edge and cloud solution that maximizes the insights gained from every IoT device. We think it’s a very powerful combination at exactly the right time.”
Device data captured by Cloud IoT Core gets published to Cloud Pub/Sub for downstream analytics. Businesses can conduct ad hoc analysis using Google BigQuery, run advanced analytics, and apply machine learning with Cloud Machine Learning Engine, or visualize IoT data results with rich reports and dashboards in Google Data Studio.
“Our integration with Google Cloud harmonizes the workload and creates new efficiencies from the edge to the cloud across a range of dimensions,” said David King, CEO at FogHorn. “This approach simplifies the rollout of innovative, outcome-based IIoT initiatives to improve organizations’ competitive edge globally, and we are thrilled to bring this collaboration to market with Google Cloud.”
by Gary Mintchell | Feb 20, 2018 | Automation, Industrial Computers, Security
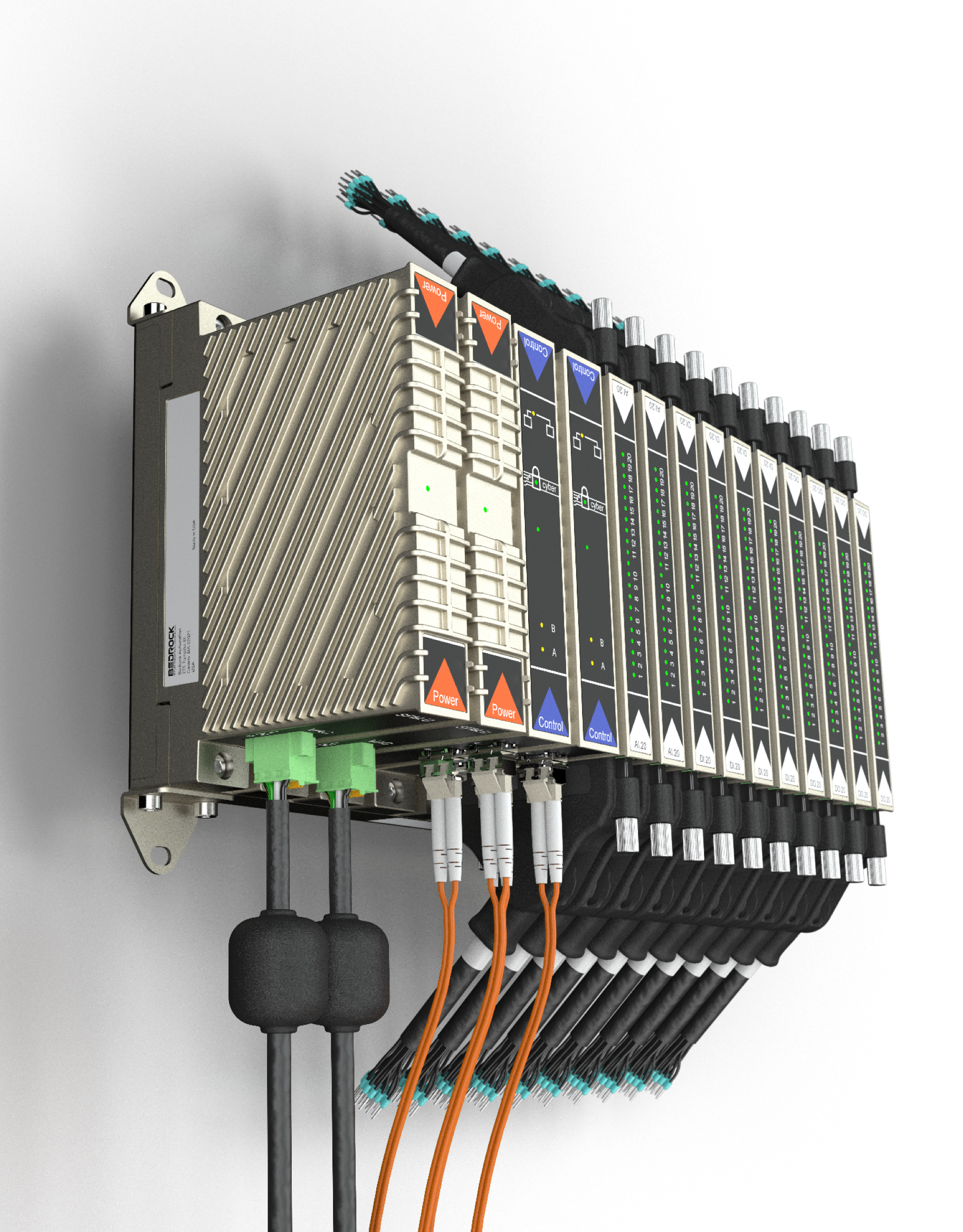
Bedrock Automation, products built for security from the chips up, had a flurry of activity at the ARC Industry Forum in Orlando last week. It announced a firmware upgrade, OPC UA and partnerships for its SCADA product, and anomaly detection. Here’s a teaser—CEO and Founder Albert Rooyakkers pulled out a new piece of hardware. He didn’t have a release or specs for me, but watch for a new, lower cost, SCADA or gateway device hardened and built with security in mind from the chips up.
Bedrock and OPC UA
Bedrock Automation has published a concise, easy-to-deploy interface specification that enables users and application developers to take advantage of the security capabilities of OPC UA communications software. By following the simple procedures outlined in the Bedrock SCADA Security Platform Specification, developers can upgrade any OPC UA compliant client into a highly secure OPC UA channel, across which users can exchange data between plant floor operations and SCADA applications. Three leading SCADA software developers, Inductive Automation, ICONICS and TATSOFT, are committing and releasing support to the Bedrock interface specification.
“OPC UA provides unique cyber security advantages enabling open communications across numerous industrial devices and applications and providing the end-users options for integrating authentication keys protecting those communications. The most secure OPC level is to authenticate those keys against a known root of trust, which Bedrock supplies via a certificate authority (CA), validated against cryptographic keys built into its controller,” said Thomas J. Burke, OPC Foundation President and Executive Director, adding “Bedrock Automation is a clear leader in supporting the OPC UA standards, and provides information integration and communication that the end users have been demanding.
Bedrock designs and sources its own secure semiconductor components with encryption and authentication technologies embedded at the “birth” of their modules, assembled and tested by Bedrock in their cyber secure supply chain. The unique design then draws on the power and flexibility of public key infrastructure (PKI) and Transport Layer Security (TLS) standards similar to those used to secure ecommerce transactions and military and aerospace electronics. Bedrock Automation then uses those securely embedded keys as the basis for digital certificates that manage access and communication between SCADA applications and control systems. Bedrock Cybershield 3.0 firmware is the first control system to offer an embedded PKI for SCADA applications.
“Such a simple specification demonstrates that Open and Secure SCADA can be deployed today, and that an applications interface does not have to be thousands or even hundreds of pages. We are pleased to be working with innovative SCADA software providers such as Inductive Automation, ICONICS and TATSOFT, to help them and their customers take advantage of the secure communications capabilities of OPC UA and the intrinsic security of the Bedrock platform,” said Rooyakkers.
Cybershield 3.0
Bedrock Automation also announced the availability of Cybershield 3.0, a major firmware upgrade with advancements that make it easier for end users and developers to build control applications that are both open and secure. Among the six major innovations facilitated by the Cybershield 3.0 upgrade are the first public key infrastructure (PKI) built into an OPC UA server for SCADA applications; an industrial Certificate Authority (CA) for user key management; virtual crypto key locks for the controller; and a Secure Proxy server capability that can protect legacy controls systems of other vendors.
“Cybershield 3.0 is one of the most significant steps forward since the release of our Bedrock OSA platform. We now support leading SCADA companies in integrating their OPC UA client to our open security and key management tools. In addition, we start our march to converge IT cyber detection technologies into real-time OT automation with our integrated Anomaly Detection (AD) tools built into every controller. We are delivering secure SCADA and AD as intrinsic and zero-cost advancements, focused acutely on ease of use and reductions in lifecycle costs,” said Bedrock founder and CEO Albert Rooyakkers.
Bedrock Cybershield 3.0 includes the following capabilities:
1) Secure Open SCADA with OPC UA. The cryptographic keys built into all the Bedrock system electronics, provide the root of trust for the Bedrock Certificate Authority (CA) that verifies the reliability of OPC UA-managed communications between SCADA and PLCs or other industrial control systems.
2) Open Certificate Authority (CA) for SCADA. This advanced SaaS key and certificate management tool is not only FREE to our customers but is simple to deploy with our Secure SCADA Interface Specification. Leading SCADA providers, including Inductive Automation, ICONICS and Tatsoft, are committing to and releasing support to this interface specification.
3) Intrusion detection. Even though the Bedrock control system has protection built into its core, users still need to know when system security is challenged. Cybershield 3.0 comes standard with intrinsic Anomaly Detection (AD) functionality that continuously monitors the controller’s network and system time to detect intrusions and anomalous behavior and report it to both SCADA and enterprise database applications for trending, alarming and historizing anomalous cyber activity.
4) Quickly Secure Legacy Automation with Secure SCADA. Companies can now use Bedrock security to help integrate open standard communications protocols with legacy PLC and DCS systems from other vendors. A Bedrock secure controller module acts as a gateway between SCADA platform workstation and the legacy controllers.
5) Cryptographic key locking. Cybershield 3.0 also includes a cryptographic controller engineering key lock that permits only users with the required credentials to change the mode of the controller.
6) Achilles and EMP compliance on power supplies. Bedrock Automation is certifying its standalone power supply and standalone uninterruptible lithium power supply to both MiL-STD-461-G, the military standard for advanced EMP hardening, and Achilles Level 2 certification, augmenting the EMP and Achilles certification achieved for its control system modules last year.
“Today’s increasingly connected environment drives the process industries to search for automation solutions that deliver the benefits of open communications with ‘baked in’ cybersecurity. By extending its secure automation technology to third-party software providers, Bedrock Automation addresses this key pain point of future automation requirements. ARC believes the intrinsic and no-cost approach of Bedrock’s cybersecurity strategy is the quintessential component missing in control systems, today,” writes ARC analyst Mark Sen Gupta in his recent report, Bedrock Automation’s Open Secure Automation a “Win” with End Users
Anomaly Detection
Bedrock Open Secure Automation (OSATM) firmware will include intrinsic Anomaly Detection (AD). Bedrock OSA AD will be available as standard integrated functionality that continuously monitors the controller’s network and system time to detect intrusions and anomalous behavior.
“Preventing control system intrusion is fundamental to holistic cyber security. In addition, users need to know when the system security is being challenged. This is the role of anomaly detection. At no additional cost or complexity for the user, Bedrock’s AD delivers additional assurance that no one is tampering with your automation,” said Rooyakkers. Bedrock Anomaly Detection includes the following functionality:
• Dynamic Port Connection Monitoring, which records all attempts to connect any controller or communication point and captures identifying information on the intruder
• Network Port Scanning, which detects if hackers are scanning for open ports that might provide access to the control network
• System Time Monitoring, which detects attepts to manipulate log files to conceal malicious activity
• Cryptographic Controller Engineering Key Lock, which permits only users with valid user credentials to change the configuration and operation mode of the controller and records all access
• Intrusion Event Logging, which records all detected anomalies and reports them to SCADA software through OPC UA and standard database access for historian, alarming, and trending functions. Additionally, a tri-color status LED on the faceplate of Bedrock Controllers provides indication locally whenever an intrusion is detected.
by Gary Mintchell | Jan 16, 2018 | Automation, Security
Cyber security is on the mind of all of us. The Internet of Things, digital factory, Industry 4.0, and all of the new strategies for improving manufacturing and production efficiencies contain a common element. They all inherently contain connections that can possibly be attacked by cyber hackers.
We are all concerned with foreign government attacks that can blow up facilities, poison water supplies, and other doomsday scenarios we can imagine. However, most hackers are really after a pay day. A big pay day. They can hold your process—and your business—hostage until you fork over some cash.
I have had many interesting cybersecurity conversations with Albert Rooyakkers, founder and CEO of Bedrock Automation. He has built a powerful controller with security designed in from the chips on up. He’s been touting the “Open Secure Automation (OSA)” platform lately.

The company just released a new white paper on the cyber security vulnerabilities and defense of industrial control systems. The 20-page document, Securing Industrial Control Systems – Best Practices, covers the threat landscape and presents a holistic approach to defending it, including assessing risk, physical security, network security, workstation and server security, as well as the fundamentals of OSA.
I just read it and found it informative. You can download it here along with the previous three papers in the series.
“As we discuss cyber security with users of automation, we find that many are aware of the threat potential but are not sure if they are doing enough to protect themselves. We saw the need for a technical paper that explains both the mindset and motives of an attacker, as well as the tools and technologies of defense. This paper defines the issues in a practical, holistic way while providing recommendations on how to begin and sustain best practices for cyber defense,” said Rooyakkers.
The first half of the paper covers conventional cyber security practices that apply to all industrial control systems. It provides an assessment of the threats, including drive-by attacks, advanced persistent threats (APTs), espionage, process attacks, and ransomware. It also looks at assessing the related risks, with an introduction to Process Hazards Analysis (PHA) and Hazards and Operability (HAZOP) methodologies used to identify malfunctions that might harm people, the process, or the environment.
To assist with risk assessment, the paper provides an overview of conventional protection practices. This includes network segmentation, firewalls, and DMZs; managing workstations, servers, end-users, and applications; and implementing active defense measures, including security event monitoring and management.
The second part of the paper is devoted to more recent techniques, based on the application of intrinsic cyber security advances that have been applied in military, aerospace, and ecommerce, and are now being used to protect industrial control systems. These create a hardware end-point root of trust that combines advanced cryptography, digital signing techniques, an industrial certificate authority, and public key infrastructure (PKIs) built into the control system to create an infrastructure for user defense.
The paper also presents the features of the Bedrock Open Secure Automation platform, which embraces the best practices discussed and details the process by which they can be applied to legacy and new systems.

by Gary Mintchell | Sep 26, 2017 | Automation, Security
Inductive Automation included a number of partner companies in its Ignition Community Conference last week in Folsom, CA. Among these companies was Bedrock Automation. I’ve written about Bedrock before a few times. This trip I was looking at its display when its CEO in disguise appeared.
Why it matters: Cyber security is at the top of everyone’s mind these days. Bedrock Automation has designed a system to be secure from all parts of the supply chain.
Albert Rooyakkers, founder/CEO/CTO, was wearing a hat and sunglasses and I walked right past him. However, he came over and gave me his usual high energy explanation of the entire Bedrock system.
Bedrock Automation builds an industrial control system (PLC) that was designed from the beginning with security in mind. Not just cyber security, but also security from tampering, lightning, high-energy electromagnetic interference, and more.
Intrinsic Security begins with Strong Cryptography, then adds Secure Components, Component Anti Tamper, Secure Firmware, Secure Communications, and Module Anti Tamper.
The metal construction showcases the secure construction, just as does the design of the I/O modules and communication with the controller (no insecure backplane).
Public Key Infrastructure
Rooyakkers always gives me the deep dive into Public Key Infrastructure which leads to Hardware Root of Trust—the essential element of security in the product.
Use of asymmetric cryptography for authentication and key exchange is the basis of secure e-commerce. In the internet context, there is a critical additional piece, a root of trust at the center of an exchange. This is called Certificate Authority. Key pairs, certificates, a root of trust and interoperable algorithms together form a Public Key Infrastructure (PKI) which includes the infrastructure and policies to manage and maintain the trust. Some of the building blocks include:
• Signatures
• Transport Layer Security
• X.509 Certificates
• Certificate Chain of Trust
• Root Certificate Authority
Until now PKI has not been implemented in industrial control systems. Bedrock Automation embeds the Hardware Root of Trust in the control system. It is designed from the ground up with security in mind.
Bedrock Automation has always gone to market with systems integrators—a strategy that fits with Inductive Automation. In many remote control and SCADA systems, the two form a perfect pair.

by Gary Mintchell | Sep 7, 2017 | Automation, Networking, News, Process Control
Here is some news regarding control and networking. Bedrock Automation is a recent entrant into the control and automation space, while Time Sensitive Networking (TSN) holds great potential to be a disruptive force.
Control
I seldom write about automation company “wins”, but this one shows some direction for a new company. Bedrock Automation is a young automation company that has built a new control platform from the ground up for not only the latest in control but also for security.
My curiosity has focused on where it would find a market. I don’t see it displacing Rockwell Automation and Siemens any time soon, but the platform is robust and adaptable. This looks like a perfect application.
Pinnacle Midstream, a Houston-based supplier of storage and processing services for the oil and gas industry, has selected the Bedrock control system as the automation platform for its crude oil receipt and delivery points. The Bedrock system will coordinate flow of product from partners, through the Pinnacle processing facilities and onto refiners and shippers. Pinnacle chose Bedrock system for its scalability, ease of engineering, ruggedness, cost efficiencies and intrinsic cyber security.
“We are expanding to the meet the growing need for midstream services and need a secure way to centralize control of flow amongst our facilities. The Bedrock system provides an economical solution in a small, easy-to-implement system that can coordinate edge control today, while also scaling easily and economically to the full DCS functionality we expect to need in the future. We also liked the rugged Bedrock housing, which will resist the dust that gets into everything around here,” said Mike Hillerman, VP of Engineering and Operations for Pinnacle Midstream.
Networking
Avnu Alliance, the industry consortium driving open standards-based deterministic networking through certification, is co-hosting the 2017 Time Sensitive Networks and Applications (TSN/A) Conference with WEKA FACHMEDIEN on September 20-21 at the Mövenpick Hotel Stuttgart Airport in Germany.
The TSN/A Conference is a combination of the “TSNA Conference” and the “Industrial Ethernet TSN Kongress” and offers attendees insights into Time-Sensitive Networks and usage in applications for Automotive, Industrial, Professional Audio/Video and more. The conference spans two days of technical sessions, panel discussions, vendor demonstrations, and participant networking.
“We are excited to bring together experts and thought leaders from around the world to the TSN/A Conference in Germany this year” said Kevin Stanton, Avnu Alliance Chairman, who will also deliver a conference presentation on Time Synchronization on Wired and Wireless Infrastructure. “It’s been a pleasure to join forces with WEKA FACHMEDIEN as the speakers present both the technology of TSN and its implications across our industries.”
On Wednesday, September 20, the first day of the conference, programming will feature two keynotes from Avnu Alliance members. Wolfgang Schenk of Hirschmann Automation and Control will present on “Time-Sensitive Networking: Enabling Technology for the Automation Model of the Future,” analyzing the transformation of the automation pyramid towards an automation pillar and discussing why TSN is the enabling technology for this transformation. Avnu Alliance Member BMW representative Dr. Kirsten Matheus will give a keynote on the “Use of AVB and TSN in the Automotive Industry.” Specifically, the presentation will describe the results of two workshops that Avnu Alliance held to gauge the need in the automotive industry for different Audio Video Bridging (AVB)/TSN functions.
I am happy to see momentum building for the technology. Can’t wait to see applications.








