
by Gary Mintchell | Oct 24, 2018 | Automation, Process Control
Our schedules finally aligned and I was able to catch up with Ed Harrington, director of the Open Process Automation Forum for The Open Group. A few months ago I talked with Gary Freburger and Peter Martin of Schneider Electric’s process automation unit. We discussed the OPAF and what had been going on since the ARC Forum in Orlando last February.
OPAF has laid out an ambitious agenda moving automation toward an era of open connectivity and interoperability.
The original plan broached a couple of years ago at ARC Forum by representatives of ExxonMobil and Lockheed Martin was to prod suppliers into reducing the problem of upgrading systems in the field without the huge expense of rip-and-replace. Considerable industry jockeying ensued. Schneider Electric (Foxboro) eventually taking a leadership position in the effort with assistance from Yokogawa and to a degree Siemens. Other suppliers are watching and evaluating.
Smaller suppliers such as Inductive Automation have become involved along with some of the major automation systems suppliers.
The OPAF specification is really a standard of standards. The group wishes to build upon existing standards, assembling them in such a way as to advance the cause of open automation.
Harrington told me that so far this year, the group has published three items (that are open to the public). One is a business guide, The Open Process Automation Business Guide: Value Proposition and Business Case for the Open Process Automation Standard.
The industrial control systems that manufacturers use to automate their processes are critical to the company’s productivity and product quality. To increase the business contribution from control systems, manufacturers need:
1. Increases in operational benefits from improved capabilities
2. Improvements in cybersecurity compared to currently available systems
3. Reductions in the system’s capital and lifecycle costs
The organization has also published The Open Group Snapshot—Open Process Automation Technical Reference Model: Technical Architecture and a white paper Requirements for an Open Process Automation Standard.
Harrington also told me to expect an announcement of further work at next week’s Open Group Quarterly Meeting in Singapore.
I have seen a number of these initiatives in my career. Few succeed in entirety. However, the thinking that goes into this work always moves industry forward. I don’t know if we’ll ever see a truly OPAF control system. Anything that brings more rationality to the market keeping in minds the goals of OPAF will do much for helping manufacturers and producers improve performance. And that’s what it’s all about.

by Gary Mintchell | Aug 24, 2018 | Automation, Operator Interface, Technology, Workforce
Simulators are great training tools. It sure beats flying 777s around for your annual pilot recert. Gaming technology has become so good along with many other technologies, that operators of process plants and machinery should be well trained to respond appropriately to any emergency.
Georgia Institute of Technology sent this information about an advancement in simulation for operator training. Good stuff.
A simulator that comes complete with a virtual explosion could help the operators of chemical processing plants – and other industrial facilities – learn to detect attacks by hackers bent on causing mayhem. The simulator will also help students and researchers understand better the security issues of industrial control systems.
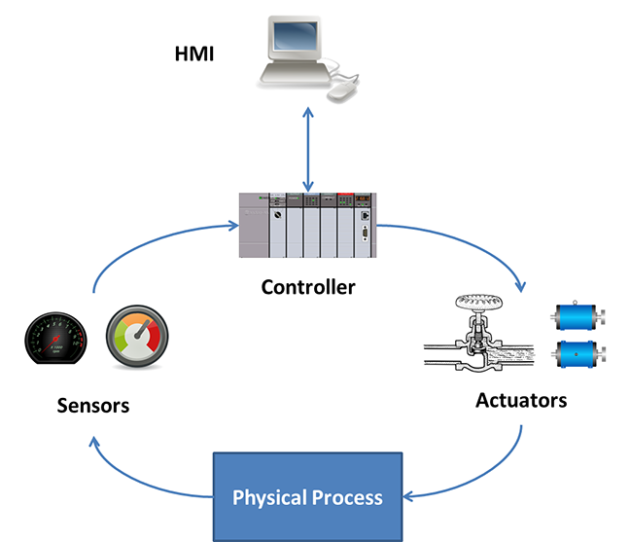
This flow chart shows data flows within a simulated chemical processing facility.
Facilities such as electric power networks, manufacturing operations and water purification plants are among the potential targets for malicious actors because they use programmable logic controllers (PLCs) to open and close valves, redirect electricity flows and manage large pieces of machinery. Efforts are underway to secure these facilities, and helping operators become more skilled at detecting potential attacks is a key part of improving security.
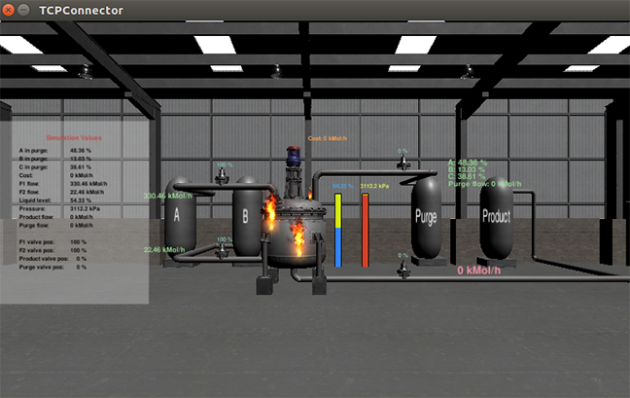
Screen captures show a simulated explosion in a chemical processing plant precipitated by a cyberattack on the system.
“The goal is to give operators, researchers and students experience with attacking systems, detecting attacks and also seeing the consequences of manipulating the physical processes in these systems,” said Raheem Beyah, the Motorola Foundation Professor in the School of Electrical and Computer Engineering at the Georgia Institute of Technology. “This system allows operators to learn what kinds of things will happen. Our goal is to make sure the good guys get this experience so they can respond appropriately.”
Details of the simulator were presented August 8 at Black Hat USA 2018, and August 13 at the 2018 USENIX Workshop on Advances in Security Education. The simulator was developed in part by Atlanta security startup company Fortiphyd Logic, and supported by the Georgia Research Alliance.
The simulated chemical processing plant, known as the Graphical Realism Framework for Industrial Control Simulations (GRFICS), allows users to play the roles of both attackers and defenders – with separate views provided. The attackers might take control of valves in the plant to build up pressure in a reaction vessel to cause an explosion. The defenders have to watch for signs of attack and make sure security systems remain operational.
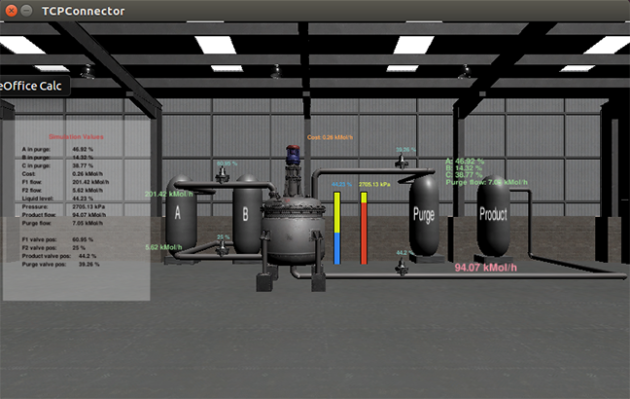
Screen capture shows a chemical processing plant in which critical parameters are rising due to false process data and control commands injected by an attacker.
Of great concern is the “man-in-the-middle” attack in which a bad actor breaks into the facility’s control system – and also takes control of the sensors and instruments that provide feedback to the operators. By gaining control of sensors and valve position indicators, the attacker could send false readings that would reassure the operators – while the damage proceeded.
“The pressure and reactant levels could be made to seem normal to the operators, while the pressure is building toward a dangerous point,” Beyah said. Though the readings may appear normal, however, a knowledgeable operator might still detect clues that the system has been attacked. “The more the operators know the process, the harder it will be to fool them,” he said.
The GRFICS system was built using an existing chemical processing plant simulator, as well as a 3D video gaming engine running on Linux virtual machines. At its heart is the software that runs PLCs, which can be changed out to represent different types of controllers appropriate to a range of facilities. The human-machine interface can also be altered as needed to show a realistic operator control panel monitoring reaction parameters and valve controller positions.
“This is a complete virtual network, so you can set up your own entry detection rules and play on the defensive side to see whether or not your defenses are detecting the attacks,” said David Formby, a Georgia Tech postdoctoral researcher who has launched Fortiphyd Logic with Beyah to develop industrial control security products. “We provide access to simulated physical systems that allow students and operators to repeatedly study different parameters and scenarios.”
GRFICS is currently available as an open source, free download for use by classes or individuals. It runs on a laptop, but because of heavy use of graphics, requires considerable processing power and memory. An online version is planned, and future versions will simulate the electric power grid, water and wastewater treatment facilities, manufacturing facilities and other users of PLCs.
Formby hopes GRFICS will expand the number of people who have experience with the security of industrial control systems.
“We want to open this space up to more people,” he said. “It’s very difficult now to find people who have the right experience. We haven’t seen many attacks on these systems yet, but that’s not because they are secure. The barrier for people who want to work in the cyber-physical security space is high right now, and we want to lower that.”
Beyah and Formby have been working for several years to increase awareness of the vulnerabilities inherent in industrial control systems. While the community still has more to do, Beyah is encouraged.
“Several years ago, we talked to a lot of process control engineers as part of the NSF’s I-Corps program,” he said. “It was clear that for many of these folks then, security was not a major concern. But we’ve seen changes, and lots of people are now taking system security seriously.”

by Gary Mintchell | Apr 4, 2018 | Security
Sometimes I wonder–Is it time for the entire Boomer generation to retire and pass the baton to the next generation? Here is another survey, this one on cybersecurity, that reveals executives know about a problem but have few or no plans to solve it soon.
People tell me constantly about surveys such as this one or training opportunities where executives and engineers in Europe pursue knowledge and those in Asia cannot satisfy their demand for standards and knowledge. And in the US? Not so much interest.
Here is a poll by a security company, Indegy, who (maybe not so surprisingly since it sells solutions) uncovered the gap yet again.
The poll found that nearly 60 percent of executives at critical infrastructure operators polled in a recent survey said they lack appropriate controls to protect their environments from security threats. As expected, nearly half of all respondents indicated their organizations plan to increase spending for industrial control system (ICS) security measures in the next 12-24 months.
“We have been tracking the escalation in cyber threat activity specifically targeting critical infrastructures for some time,” says Barak Perelman, CEO of Indegy. “As the recent joint DHS/FBI CERT Technical Alert illustrates, adversaries have compromised facilities across the US to conduct reconnaissance and likely develop “Red Button” capability for future attacks.”
Lack of Visibility and Control Cited
While organizations have made significant investments to secure their IT infrastructures, they have not fully addressed threats to operational technology (OT) environments. The recent Indegy poll of nearly 100 executives from various critical infrastructure organizations underscores the lack of preparedness in key sectors including energy, utilities and manufacturing. Among the key findings:
- 35% of respondents said they have little visibility into the current state of security within their environment, while 23% reported they have no visibility
- 63% claimed that insider threats and misconfigurations are the biggest security risks they currently face
- 57% said they are not confident that their organization, and other infrastructure companies, are in control of OT security
- Meanwhile, 44% of respondents indicated an increase in ICS spending was planned in the next 12 to 24 months, with 29% reporting they were not sure
by Gary Mintchell | Feb 20, 2018 | Automation, Industrial Computers, Security
Bedrock Automation, products built for security from the chips up, had a flurry of activity at the ARC Industry Forum in Orlando last week. It announced a firmware upgrade, OPC UA and partnerships for its SCADA product, and anomaly detection. Here’s a teaser—CEO and Founder Albert Rooyakkers pulled out a new piece of hardware. He didn’t have a release or specs for me, but watch for a new, lower cost, SCADA or gateway device hardened and built with security in mind from the chips up.
Bedrock and OPC UA
Bedrock Automation has published a concise, easy-to-deploy interface specification that enables users and application developers to take advantage of the security capabilities of OPC UA communications software. By following the simple procedures outlined in the Bedrock SCADA Security Platform Specification, developers can upgrade any OPC UA compliant client into a highly secure OPC UA channel, across which users can exchange data between plant floor operations and SCADA applications. Three leading SCADA software developers, Inductive Automation, ICONICS and TATSOFT, are committing and releasing support to the Bedrock interface specification.
“OPC UA provides unique cyber security advantages enabling open communications across numerous industrial devices and applications and providing the end-users options for integrating authentication keys protecting those communications. The most secure OPC level is to authenticate those keys against a known root of trust, which Bedrock supplies via a certificate authority (CA), validated against cryptographic keys built into its controller,” said Thomas J. Burke, OPC Foundation President and Executive Director, adding “Bedrock Automation is a clear leader in supporting the OPC UA standards, and provides information integration and communication that the end users have been demanding.
Bedrock designs and sources its own secure semiconductor components with encryption and authentication technologies embedded at the “birth” of their modules, assembled and tested by Bedrock in their cyber secure supply chain. The unique design then draws on the power and flexibility of public key infrastructure (PKI) and Transport Layer Security (TLS) standards similar to those used to secure ecommerce transactions and military and aerospace electronics. Bedrock Automation then uses those securely embedded keys as the basis for digital certificates that manage access and communication between SCADA applications and control systems. Bedrock Cybershield 3.0 firmware is the first control system to offer an embedded PKI for SCADA applications.
“Such a simple specification demonstrates that Open and Secure SCADA can be deployed today, and that an applications interface does not have to be thousands or even hundreds of pages. We are pleased to be working with innovative SCADA software providers such as Inductive Automation, ICONICS and TATSOFT, to help them and their customers take advantage of the secure communications capabilities of OPC UA and the intrinsic security of the Bedrock platform,” said Rooyakkers.
Cybershield 3.0
Bedrock Automation also announced the availability of Cybershield 3.0, a major firmware upgrade with advancements that make it easier for end users and developers to build control applications that are both open and secure. Among the six major innovations facilitated by the Cybershield 3.0 upgrade are the first public key infrastructure (PKI) built into an OPC UA server for SCADA applications; an industrial Certificate Authority (CA) for user key management; virtual crypto key locks for the controller; and a Secure Proxy server capability that can protect legacy controls systems of other vendors.
“Cybershield 3.0 is one of the most significant steps forward since the release of our Bedrock OSA platform. We now support leading SCADA companies in integrating their OPC UA client to our open security and key management tools. In addition, we start our march to converge IT cyber detection technologies into real-time OT automation with our integrated Anomaly Detection (AD) tools built into every controller. We are delivering secure SCADA and AD as intrinsic and zero-cost advancements, focused acutely on ease of use and reductions in lifecycle costs,” said Bedrock founder and CEO Albert Rooyakkers.
Bedrock Cybershield 3.0 includes the following capabilities:
1) Secure Open SCADA with OPC UA. The cryptographic keys built into all the Bedrock system electronics, provide the root of trust for the Bedrock Certificate Authority (CA) that verifies the reliability of OPC UA-managed communications between SCADA and PLCs or other industrial control systems.
2) Open Certificate Authority (CA) for SCADA. This advanced SaaS key and certificate management tool is not only FREE to our customers but is simple to deploy with our Secure SCADA Interface Specification. Leading SCADA providers, including Inductive Automation, ICONICS and Tatsoft, are committing to and releasing support to this interface specification.
3) Intrusion detection. Even though the Bedrock control system has protection built into its core, users still need to know when system security is challenged. Cybershield 3.0 comes standard with intrinsic Anomaly Detection (AD) functionality that continuously monitors the controller’s network and system time to detect intrusions and anomalous behavior and report it to both SCADA and enterprise database applications for trending, alarming and historizing anomalous cyber activity.
4) Quickly Secure Legacy Automation with Secure SCADA. Companies can now use Bedrock security to help integrate open standard communications protocols with legacy PLC and DCS systems from other vendors. A Bedrock secure controller module acts as a gateway between SCADA platform workstation and the legacy controllers.
5) Cryptographic key locking. Cybershield 3.0 also includes a cryptographic controller engineering key lock that permits only users with the required credentials to change the mode of the controller.
6) Achilles and EMP compliance on power supplies. Bedrock Automation is certifying its standalone power supply and standalone uninterruptible lithium power supply to both MiL-STD-461-G, the military standard for advanced EMP hardening, and Achilles Level 2 certification, augmenting the EMP and Achilles certification achieved for its control system modules last year.
“Today’s increasingly connected environment drives the process industries to search for automation solutions that deliver the benefits of open communications with ‘baked in’ cybersecurity. By extending its secure automation technology to third-party software providers, Bedrock Automation addresses this key pain point of future automation requirements. ARC believes the intrinsic and no-cost approach of Bedrock’s cybersecurity strategy is the quintessential component missing in control systems, today,” writes ARC analyst Mark Sen Gupta in his recent report, Bedrock Automation’s Open Secure Automation a “Win” with End Users
Anomaly Detection
Bedrock Open Secure Automation (OSATM) firmware will include intrinsic Anomaly Detection (AD). Bedrock OSA AD will be available as standard integrated functionality that continuously monitors the controller’s network and system time to detect intrusions and anomalous behavior.
“Preventing control system intrusion is fundamental to holistic cyber security. In addition, users need to know when the system security is being challenged. This is the role of anomaly detection. At no additional cost or complexity for the user, Bedrock’s AD delivers additional assurance that no one is tampering with your automation,” said Rooyakkers. Bedrock Anomaly Detection includes the following functionality:
• Dynamic Port Connection Monitoring, which records all attempts to connect any controller or communication point and captures identifying information on the intruder
• Network Port Scanning, which detects if hackers are scanning for open ports that might provide access to the control network
• System Time Monitoring, which detects attepts to manipulate log files to conceal malicious activity
• Cryptographic Controller Engineering Key Lock, which permits only users with valid user credentials to change the configuration and operation mode of the controller and records all access
• Intrusion Event Logging, which records all detected anomalies and reports them to SCADA software through OPC UA and standard database access for historian, alarming, and trending functions. Additionally, a tri-color status LED on the faceplate of Bedrock Controllers provides indication locally whenever an intrusion is detected.
by Gary Mintchell | Jan 16, 2018 | Automation, Security
Cyber security is on the mind of all of us. The Internet of Things, digital factory, Industry 4.0, and all of the new strategies for improving manufacturing and production efficiencies contain a common element. They all inherently contain connections that can possibly be attacked by cyber hackers.
We are all concerned with foreign government attacks that can blow up facilities, poison water supplies, and other doomsday scenarios we can imagine. However, most hackers are really after a pay day. A big pay day. They can hold your process—and your business—hostage until you fork over some cash.
I have had many interesting cybersecurity conversations with Albert Rooyakkers, founder and CEO of Bedrock Automation. He has built a powerful controller with security designed in from the chips on up. He’s been touting the “Open Secure Automation (OSA)” platform lately.

The company just released a new white paper on the cyber security vulnerabilities and defense of industrial control systems. The 20-page document, Securing Industrial Control Systems – Best Practices, covers the threat landscape and presents a holistic approach to defending it, including assessing risk, physical security, network security, workstation and server security, as well as the fundamentals of OSA.
I just read it and found it informative. You can download it here along with the previous three papers in the series.
“As we discuss cyber security with users of automation, we find that many are aware of the threat potential but are not sure if they are doing enough to protect themselves. We saw the need for a technical paper that explains both the mindset and motives of an attacker, as well as the tools and technologies of defense. This paper defines the issues in a practical, holistic way while providing recommendations on how to begin and sustain best practices for cyber defense,” said Rooyakkers.
The first half of the paper covers conventional cyber security practices that apply to all industrial control systems. It provides an assessment of the threats, including drive-by attacks, advanced persistent threats (APTs), espionage, process attacks, and ransomware. It also looks at assessing the related risks, with an introduction to Process Hazards Analysis (PHA) and Hazards and Operability (HAZOP) methodologies used to identify malfunctions that might harm people, the process, or the environment.
To assist with risk assessment, the paper provides an overview of conventional protection practices. This includes network segmentation, firewalls, and DMZs; managing workstations, servers, end-users, and applications; and implementing active defense measures, including security event monitoring and management.
The second part of the paper is devoted to more recent techniques, based on the application of intrinsic cyber security advances that have been applied in military, aerospace, and ecommerce, and are now being used to protect industrial control systems. These create a hardware end-point root of trust that combines advanced cryptography, digital signing techniques, an industrial certificate authority, and public key infrastructure (PKIs) built into the control system to create an infrastructure for user defense.
The paper also presents the features of the Bedrock Open Secure Automation platform, which embraces the best practices discussed and details the process by which they can be applied to legacy and new systems.












