
by Gary Mintchell | Jul 25, 2019 | Commentary, News, Security
The International Society of Automation (ISA) held a press conference today to announce the first Founding Members of its new Global Cybersecurity Alliance (GCA): Schneider Electric, Rockwell Automation, Honeywell, Johnson Controls, Claroty, and Nozomi Networks.
As we would expect, the speakers emphasized the importance of standards as the foundation for work in the Alliance. Speakers also tied in safety and productivity as partners with cybersecurity in protecting and improving manufacturing and critical infrastructure facilities and processes. I’m not so sure just exactly what the Alliance will accomplish, but if it succeeds in just raising awareness and a sense of urgency among companies it the industries, it will have accomplished an important task.
ISA created the Global Cybersecurity Alliance to advance cybersecurity readiness and awareness in manufacturing and critical infrastructure facilities and processes. The Alliance brings end-user companies, automation and control systems providers, IT infrastructure providers, services providers, and system integrators and other cybersecurity stakeholder organizations together to proactively address growing threats.
ISA is the developer of the ANSI/ISA 62443 series of automation and control systems cybersecurity standards, which have been adopted by the International Electrotechnical Commission as IEC 62443 and endorsed by the United Nations. The standards define requirements and procedures for implementing electronically secure automation and industrial control systems and security practices and assessing electronic security performance. The standards approach the cybersecurity challenge in a holistic way, bridging the gap between operations and information technology.
Leveraging the ISA/IEC 62443 standards, the Global Cybersecurity Alliance will work to increase awareness and expertise, openly share knowledge and information, and develop best practice tools to help companies navigate the entire lifecycle of cybersecurity protection. The Alliance will work closely with government agencies, regulatory bodies, and stakeholder organizations around the world.
“Accelerating and expanding globally relevant standards, certification, and education programs will increase workforce competence, and help end users identify gaps, reduce risks, and ensure they have the tools and systems they need to protect their facilities and installations,” said Mary Ramsey, ISA Executive Director. “Through the proliferation of standards and compliance programs, we will strengthen our global cyber culture and transform the way industry identifies and manages cybersecurity threats and vulnerabilities to their operations.”
The press release notes that first Founding Members of the Alliance are leading multi-national, industrial-technology providers with deep expertise in technology and applications, and they’ll apply their experience and knowledge to accomplish the Alliance’s priorities. However, two of the members were represented by building automation divisions. Two of the members are cybersecurity suppliers. Rockwell Automation is a pure play factory and process automation company and its Maverick Technologies division has been an ardent supporter of ISA. Schneider Electric is a large, multi-disciplined company, and I’m not sure which division within it is the sponsor.
“Participating in the Alliance truly shows the commitment our founding members have to the safety and security of the industrial ecosystem, as well as the criticality of collectively moving forward together to ensure the standards, best practices and methods are applied,” Ramsey said.
“ISA engaged with discussions, initiated by Schneider Electric, to create an ISA-led global, open and industry-wide alliance comprised of all cybersecurity stakeholder companies. ISA quickly expanded those conversations to include Rockwell Automation, Honeywell, Johnson Controls, Claroty, and Nozomi Networks. These first Founding Members have since worked together to help us define the Alliance’s objectives. We are thankful for their collaboration and commitment. Together we welcome companies and organizations from all segments of industry to join our efforts.”
The Alliance is seeking additional members to support its initiatives. End-user companies, asset owners, automation and control systems providers, IT infrastructure providers, services providers, and system integrators and other cybersecurity stakeholder organizations are invited to join. Annual contributions to fund initiatives are based on company revenues and are tax-deductible.
Perspectives: Quotes from the ISA Global Cybersecurity Alliance Founding Members
“Over the last few years, global industry has recognized that taking on increasingly dangerous cyber risks can’t be limited to a single company, segment, or region. However, until now, there has been limited ability to respond as a unified whole to these worldwide threats. But by establishing an open, collaborative, and transparent body, with a focus on strengthening people, processes, and technology, we can drive true cultural change. We are pleased that ISA has stepped forward, and we look forward to working openly and collaboratively with them, our fellow Founding Members, and many others affiliated with global industry, especially end users. Together we will bring to bear the standards-based technology, expertise, and special skills required to better secure and protect the world’s most critical operations and the people and communities we serve.” — Klaus Jaeckle, Chief Product Security Officer, Schneider Electric
“Cybersecurity is critical to digital transformation. It’s critical not only for the protection of information and intellectual property, but also for the protection of physical assets, the environment, and worker safety. We make it a priority to collaborate with partners and research institutions to develop secure products. Rockwell Automation participated in the development of the 62443 standards from the beginning and continues to support ISA cybersecurity initiatives. Our engagement with the Global Cybersecurity Alliance will be another important step in our efforts to help customers identify and mitigate risks.” — Blake Moret, CEO, Rockwell Automation
“Cybersecurity is the great equalizer to all companies. It’s critical to the connected world we live in and the cornerstone of trust that the world needs to be able to operate. Whether protecting critical infrastructure or managing a building’s operations, users need to do this with the confidence the employed systems are robust and secure. We are committed to and proud to work together ISA and the GCA members to continue to drive the adoption of the ISA/IEC 62443 series of standards and identify further ways to secure and protect the connected world which we live. At Honeywell, we see cybersecurity as a core part of the future we are making, and we see the GCA as an important way to work together to make that happen.” — Matthew Bohne, Vice President and Chief of Product Security, Honeywell Building Technologies
“Digital transformation in the building sector continues to accelerate, which heightens the urgency for cybersecurity across the industry and beyond. As a leader in the industrial automation controls business, Johnson Controls is already a strategic member of the ISASecure program and is consistently taking proactive actions to protect customers against cyber-threats and risks. Joining ISA Global Cybersecurity Alliance is a necessary and meaningful step as it supports our company values, customer adoption of the ISA/IEC 62443 standard and efforts to educate global government and regulatory bodies. We are proud to solidify our commitment to this important effort.” — Jason Christman, Vice President, Chief Product Security Officer, Global Products, Johnson Controls
“One of the most effective ways to drive consistency in an industry is by putting standards in place, and we’re looking forward to collaborating with all of these founding members, as well as future Alliance members, to help drive global best-practices forward in this historically standard-less environment. Claroty is committed to the mission of protecting all IoT and OT networks from cyber risks. Through our work with the Global Cybersecurity Alliance, we will be able to help shape the future of cybersecurity in these high-risk industries.” — Dave Weinstein, Chief Security Officer, Claroty
“Nozomi Networks believes real community collaboration, actionable standards and effective education are key ensuring a secure future for industrial organizations around the world. That’s why we are helping develop secure-by-design standards as a working member of ISA99 standards committees, why we’ve designed our industrial cyber security solutions for easy integration across the broadest possible set of industrial and IT technologies; and why we are thrilled to help establish the Global Cybersecurity Alliance. Together we will build a secure future for the industrial infrastructure that runs the world.” — Andrea Carcano, Nozomi Networks Co-founder and Chief Product Officer

by Gary Mintchell | May 30, 2019 | Manufacturing IT, News, Security
Cyber Security got a shout-out during the Siemens Spotlight on Innovation forum in Orlando last week. Leo Simonovich, VP and Global Head, Industrial Cyber and Digital Security at Siemens Gas and Power, and Mike Wiacek, co-founder & CSO of Chronicle (an Alphabet company) took the stage discussing their newly signed cyber security agreement.
Key phrase—“customers can own their environment”. Perhaps the most interesting conversation I had during the networking event was with a Chronicle tech person who gave me a deep dive into the product. This is security unlike everything else I investigate in the OT realm. This isn’t a network monitoring app. Nor is it a device that acts as a firewall for industrial control devices. It builds a huge database and adds analytics (which is “in our DNA”). The solution has two parts—visibility and context. It bridges IT and OT worlds with the intent to “democratize security for the success of the digital economy”; that is, make it accessible to customers, simple, affordable, easy-to-use.
Through a unified approach that will leverage Chronicle’s Backstory platform and Siemens’ strength in industrial cyber security, the combined offering gives energy customers unparalleled visibility across information technology (IT) and operational technology (OT) to provide operational insights and confidentially act on threats.
The energy industry has historically been unable to centrally apply analytics to process data streams, cost-effectively store and secure data, and identify malicious threats within OT systems. Research conducted by Siemens and Ponemon Institute found that while 60 percent of energy companies want to leverage analytics, only 20 percent are utilizing any analytics to do security monitoring in the OT environment. Small and medium enterprises are particularly vulnerable to security breaches as they frequently do not have the internal expertise to manage and address increasingly sophisticated attacks.
“The innovative partnership between Siemens and Chronicle demonstrates a new frontier in applying the power of security analytics to critical infrastructure that is increasingly dependent on digital technology,” said Simonovich. “Cyber-attacks targeting energy companies have reached unprecedented speeds, and our cutting-edge managed service unlocks the analytics ecosystem offers a new level of protection from potential operational, business and safety losses.”
“Energy infrastructure is an obvious example of cyber-attacks affecting the physical world and directly impacting people’s lives,” said Ansh Patnaik, Chief Product Officer, Chronicle. “Backstory’s security telemetry processing capabilities, combined with Siemens’ deep expertise, gives customers new options for protecting their operations.”
The partnership between Siemens and Chronicle will help energy companies securely and cost-effectively leverage the cloud to store and categorize data, while applying analytics, artificial intelligence, and machine learning to OT systems that can identify patterns, anomalies, and cyber threats. Chronicle’s Backstory, a global security telemetry platform for investigation and threat hunting, will be the backbone of Siemens managed service for industrial cyber monitoring, including in both hybrid and cloud environments. This combined solution enables security across the industry’s operating environment – from energy exploration and extraction to power generation and delivery.

by Gary Mintchell | Nov 27, 2018 | Manufacturing IT, Operations Management, Software
I’m still deep in cyber security meetings in Germany. A pause here for software and cloud news from the west coast of America—OSIsoft and Amazon Web services. Since PI is used by many industrial companies, these announcements reveal the deep acceptance of cloud technologies.
In short, here are three bullets:
- AWS Quick Starts for PI System: enables industrial customers to quickly deploy and manage the PI System on AWS.
- PI Integrator for Business Analytics: optimized for AWS to reduce time and cost of bringing operational and IoT data to AWS for sharing or advanced analytics.
- Enhanced connectivity and data sharing to accelerate digital transformation and shrink the OT-IT gap.
OSIsoft launched a suite of products today designed to enable manufacturers, utilities, and other industrial customers to run the OSIsoft PI System on Amazon Web Services.
AWS Quick Starts for the PI System consists of AWS CloudFormation templates, scripts, and reference architectures for quickly spinning up and managing a fully functioning PI System on AWS. Customers will use the PI System Quick Starts for moving PI System workloads to the AWS cloud or for providing an aggregate PI System across an enterprise, monitoring remote or isolated assets and enabling data science efforts.
The PI Integrator for Business Analytics, meanwhile, has been optimized to extract, clean and transmit data from PI Systems and reduce data preparation tasks that bog down big data and data science initiatives. Some customers have successfully used PI Integrator technology to reduce the time consumed by data preparation in advanced analytics projects by over 90%.
AWS Quick Starts will be available in 2019. PI Integrator for Business Analytics, previewed at Hannover Messe earlier this year, is available this month.
Under the Hood
Quick Starts are built by AWS solutions architects and partners to help deploy solutions on AWS, based on AWS best practices for security and high availability. These reference deployments implement key technologies automatically on the AWS Cloud, often with a single click and in less than an hour. You can build your test or production environment in a few steps, and start using it immediately.
The PI Integrator for Business Analytics can integrate to Amazon S3, Amazon Redshift, and Amazon Kinesis Data Streams, enabling industrial customers to speed up their data science experiments, combine disparate data sets for business intelligence, and operationalize the outcomes of advanced analytics that augment decision making.
The Life of the PI System
OSIsoft’s PI System transforms the vast number of operational data streams from sensors, devices and industrial processes into rich, real-time insights to help people save money, increase productivity or create connected products and services.
The PI System can be found inside thousands of companies and complex industrial sites around the globe. OSIsoft customers have used PI System technology to predict wind turbine failures, increase output at an iron mine by $120 million in a single year by fine-tuning logistics, reduce the power consumed by a supercomputer center at a national laboratory, deliver water services to millions of new customers in a major metropolitan city, transform how medicines are produced and reduce the time and expense and improve the quality and consistency of beer. Over 1,000 leading utilities, 90% of the world’s largest oil and gas companies and 65% of the Fortune 500 industrial companies rely the PI System in their operations.
“Worldwide, over 2 billion sensor-based data streams are managed by the PI System with some customers monitoring over 25 million data streams.
“Data from operations—the information being generated by chemical reactors, transformers and other industrial devices—is incredibly valuable. Operations data will be the most valuable asset companies have for moving ahead of the competition in the future. Until recently, this data has been mostly confined to the factory floor or production line in part because of the size, scope and complexity of the data generated by operations,” said John Baier, Director of Integration Technologies, Cloud Analytics Practice at OSIsoft. “Working with Amazon Web Services, we want to unlock the value of operations data by eliminating barriers and bringing it to as many people as possible.”
www.osisoft.com

by Gary Mintchell | Jun 12, 2018 | News, Organizations
This story is all about partnerships and collaboration. I started to write it yesterday morning, but then I saw a tweet, no not from the “big guy” but from PTC about the Rockwell Automation investment. I wanted to talk about the current trend of partnering.
It begins Roy Kok and DreamReports. We’ve chatted a little about how a company with a somewhat narrowly defined product and market can grow. He’s out in San Diego this week at the Rockwell Automation TechEd event. Rockwell is an important partner. All that data from IoT and analytics isn’t worth the storage if the information can’t be parsed and displayed. Enter Dream Reports. Kok assures me that there will be more partnerships in the future. It’s no doubt his best potential.
Another Rockwell Investment
Meanwhile, I had the opportunity to speak with Patrick McBride the CMO of Claroty about another Rockwell Automation investment. Once again a somewhat narrowly defined market—cyber security—using partnerships to grow. In this case, Claroty attracted $60M of Series B investment, bringing its total funding to $93 Million. He told me that the investment funds will be used to make the appropriate hires to expand sales and projects globally and to support its new partners.
The round was led by Temasek and included Rockwell Automation, Aster Capital (born out of Schneider Electric Ventures), Next47 (Siemens-backed global venture firm), Envision Ventures, and Tekfen Ventures. Original Claroty investors Bessemer Venture Partners, Team8, Innovation Endeavors, and ICV all participated in the round.
Founded in 2014 and exiting stealth mode in late 2016, this investment comes on the heels of a breakout year for Claroty capped by a 300% year-over-year growth in bookings and customer base. Claroty now has large-scale customers with production installations across six continents in nine market segments, including electric utilities, oil and gas, chemical, water, manufacturing, food and beverage, mining, and real estate (building management systems, data centers, warehouses).
“Our unparalleled investor syndicate, which includes some of the most important industrial companies in the world, is a ringing endorsement of Claroty’s technology and the progress our team has made,” said Amir Zilberstein, Claroty Co-founder and CEO. “Our mission is to protect the most critical networks on the planet and our comprehensive platform provides our customers with the capabilities they need to accomplish this vitally important task.”
This rapidly expanding cybersecurity market segment is the result of a “perfect storm” that has placed industrial networks running critical global infrastructures in the spotlight. Old and insecure industrial control networks, which used to be “air-gapped,” are now being rapidly connected to networks and exposed to a range of risks. Because of their criticality, these networks are increasingly targeted by advanced nation-state adversaries who are determined to harvest information and gain a persistent presence for potential future attacks. In 2017, industrial networks also became collateral damage in ransomware attacks like WannaCry and NotPetya costing companies billions in losses.
“A perimeter defense to cybersecurity in today’s connected world is not enough. An end-to-end approach, with solutions that provide deep visibility into operational technology and industrial control systems, is critical for the security of heavy processing environments,” said Hervé Coureil, Chief Digital Officer at Schneider Electric. “Leading the digital transformation of energy management and automation, Schneider Electric takes cybersecurity very seriously and the partnership with Claroty complements the cybersecurity layer of our IoT-enabled EcoStruxure architecture.”
“Protecting the critical automation systems our customers operate against cyberattacks remains a top priority for the company,” said Frank Kulaszewicz, SVP, Architecture & Software at Rockwell Automation. “Claroty has been a partner since 2016 and their advanced technology is a key element of our real-time threat detection and monitoring service. Our investment in Claroty is a logical extension of our ongoing strategic partnership.”
Claroty’s comprehensive cybersecurity platform provides extreme visibility into industrial networks and combines secure remote access with continuous monitoring for threats and vulnerabilities – enabling industrial control system operators to protect these important networks. The company will use investment proceeds to grow the Claroty brand globally, extend its sales and customer support footprint, and continue its rapid pace of product innovation.
T.J. Rylander, Partner at Next47, the Siemens-backed global venture firm said, “The recent increase in scale, scope, and frequency of cyberattacks on critical infrastructure has led to an uptick in demand for new solutions from companies around the world. Claroty has the team, technology, and market traction to deliver the kind of lasting impact that we are looking for at Next47.”

by Gary Mintchell | Apr 12, 2018 | Internet of Things, Manufacturing IT, Software
The Internet of Things ecosystem is changing computing in almost a seismic shift. But like geology, it builds up over time and then the event happens before you know it.
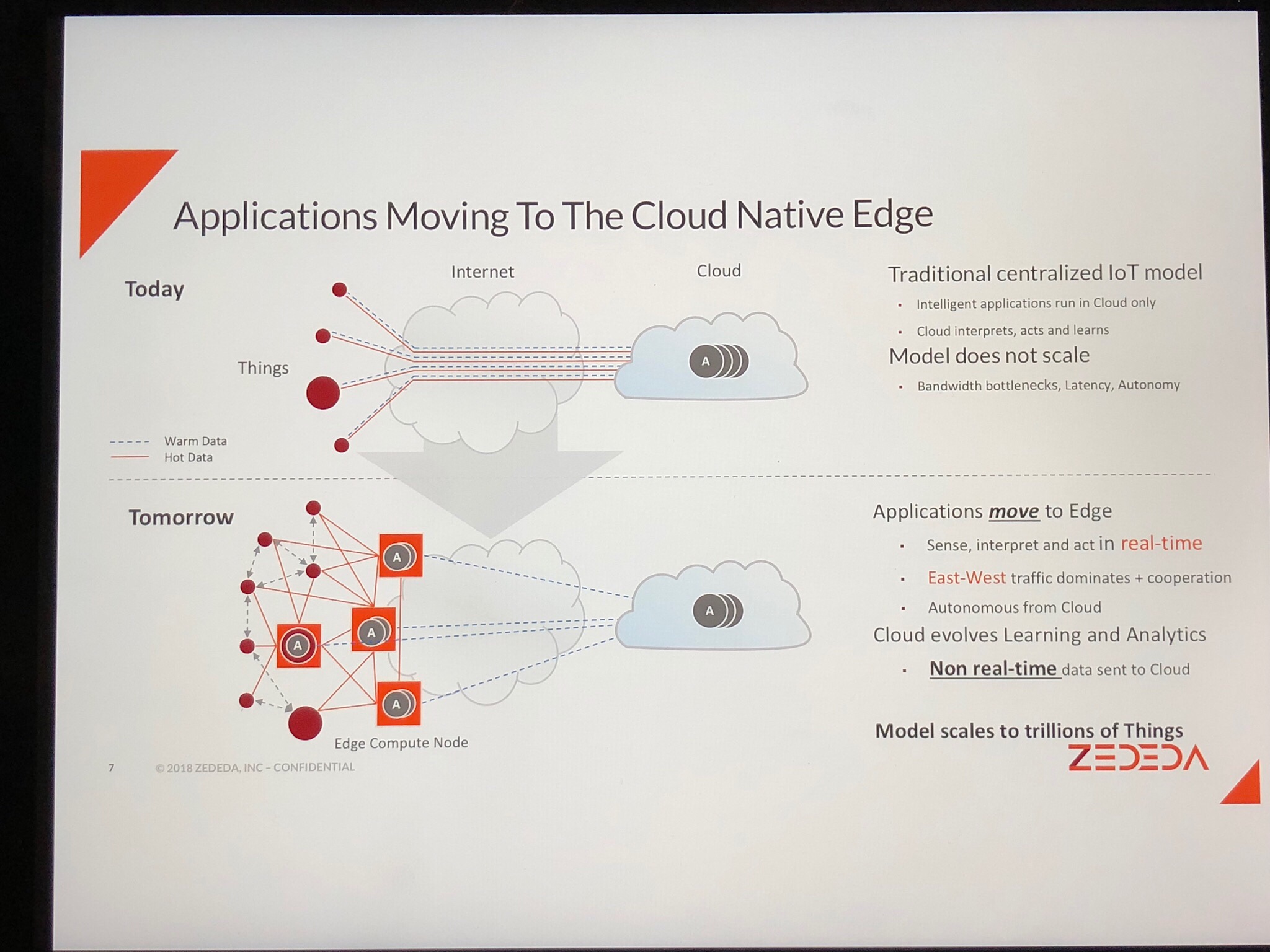
We had centralized, on-site computing revolutionized by PCs. We networked PCs and wound up with centralized computing in the cloud. Demands from building the Internet of Things (or Industrial Internet of Things for us manufacturing and production geeks) expose the flaws of cloud computing. The next hot thing—edge.
Yesterday the CEO/co-founder of Zededa talked with me about the computing platform his company is building with no less a mission than to build the largest computing company on Earth without owning infrastructure. Its vision—create a new edge economy that allows applications to run anywhere.
Some of what follows may sound familiar. I’ve talked with many companies doing a piece of what Zededa has laid out, but none are as audacious as this.
In brief, Zedeta…
- Closes $3.06M in Seed Funding
- Pioneering a secure, cloud-native approach to real-time edge applications at hyperscale for solutions ranging from self-driving cars to industrial robots
- Built a team comprised of distinguished engineers from top tech companies in cloud, networking and open source to solve the edge computing puzzle and disrupt the status quo
- Seed round was led by Wild West Capital; other investors include Almaz Capital, Barton Capital and Industry Veteran Ed Zander, former CEO of Motorola and former COO of Sun Microsystems
“Tomorrow’s edge computing environment that enables digital transformation will be distributed, autonomous and cooperative. The edge is complex and not only has to scale out securely, but simultaneously must become friendlier for app developers. That’s the problem we are solving at ZEDEDA,” stated ZEDEDA CEO and Co-Founder Said Ouissal. “It will require a drastic shift from today’s embedded computing mindset to a more secure-by-design, cloud-native approach that unlocks the power of millions of cloud app developers and allows them to digitize the physical world as billions of ‘things’ become smart and connected.”
ZEDEDA will use the funding for continued research and product development, investment in community open-source projects for edge computing as well as further investment in sales and marketing initiatives. ZEDEDA investors include Wild West Capital and Almaz Capital, whose funding was part of a broader group investors, some of whom also invested in IoT/edge companies Theatro and Sensity Systems (now Verizon).
In the coming wave of pervasive computing, real-time apps, cyber-physical systems and data services such as machine learning and analytics will become commonplace. ZEDEDA envisions an open ecosystem and a completely new technology stack that creates a service fabric essential to achieving the hyperscale that will be required in edge computing.
To realize that goal, ZEDEDA has pulled together a distinguished roster of industry veterans from legendary technology companies with expertise in areas of operating systems, virtualization, networking, security, blockchain, cloud and application platforms. This unique blend of skills combines with the team’s deep connections to core open-source projects and standardization bodies. The team’s work has directly contributed to software and system patents as well as industry standards used by billions of people around the world today.
“A new paradigm and massive innovation is needed to meet demand for IoT and edge computing,” said Kevin DeNuccio, Founder of Wild West Capital and ZEDEDA’s lead investor. “Massive shifts in technology, including the proliferation of IoT, paves the way for industry disruption, which large incumbents tend to inhibit. Disruption takes a combination of an entrepreneurial team with a very unique set of collective experience, groundbreaking ideas, and the ability to garner immediate traction with global industrial leaders, who can transform their business with machine learning and artificial intelligence delivered by the Edge connected IoT world. ZEDEDA is simply one of the most promising edge computing startups out there.”
“Operations Technology teams face major challenges when it comes to fully realizing the advantages of an IoT world. Their worlds are becoming massively connected systems dealing with virtualization, networking and security,” stated Christian Renaud, Research Director, IoT at 451 Research. “Our recent research shows that while OT teams have the application plans for leveraging IoT, the vast majority of organizations’ IT resources and capabilities are maxed out. This leaves open the question of how these edge applications and IoT will scale out without compromising security or taxing resources even further in the future.”
Ouissal told me, “Edge is the next big wave, bigger than cloud, simply because of the sheer size of the number of devices. The goal is ubiquitous compute where applications want to interact real-time. The problem with the cloud is that it’s centralized. This ecosystem is truly Cyberphysical—just like your Industry 4.0.”
The current IoT model of sending all data to the cloud for processing, won’t scale due to:
- Bandwidth
- Latency
- Privacy issues
Three problems that the company is attacking:
1. Moving apps now running in the cloud to the edge
2. Edge-to-edge communication, key for autonomous systems, peer-to-peer
3. Security, cloud requires cyber security, but at the edge we must add physical security—someone could walk in and carry out an intelligent device
Ouissal often mentioned the need to rethink management of the edge. There exists a big difference between managing cloud and edge. Zedeta is tacking the variety of management challenges for updating and managing thousands to millions of embedded devices.
Solutions the team are developing include:
1. Security-built on platform, use keys, trusted, health check with every plug in, embedded virtualization
2. management-virtualization->can run multiple sessions on a device, eg robot motion on one session and analytics on another all on same embedded system, can scale this to millions of devices
3. Networking-monitor, watch lists, anomaly detection, analyze why, VPN architecture
This is all fascinating. I can’t wait to talk with competitors and potential competitors in a couple of weeks in Hannover and during some upcoming trips to get responses.








