by Gary Mintchell | Mar 20, 2017 | Automation, Process Control, Software
Change management is a huge issue in automation and control. Who makes the change, when, what was done, was it authorized, and more questions. I’ve had many chats with leaders of companies who provide change management tools over the years. Here is a Honeywell solution.

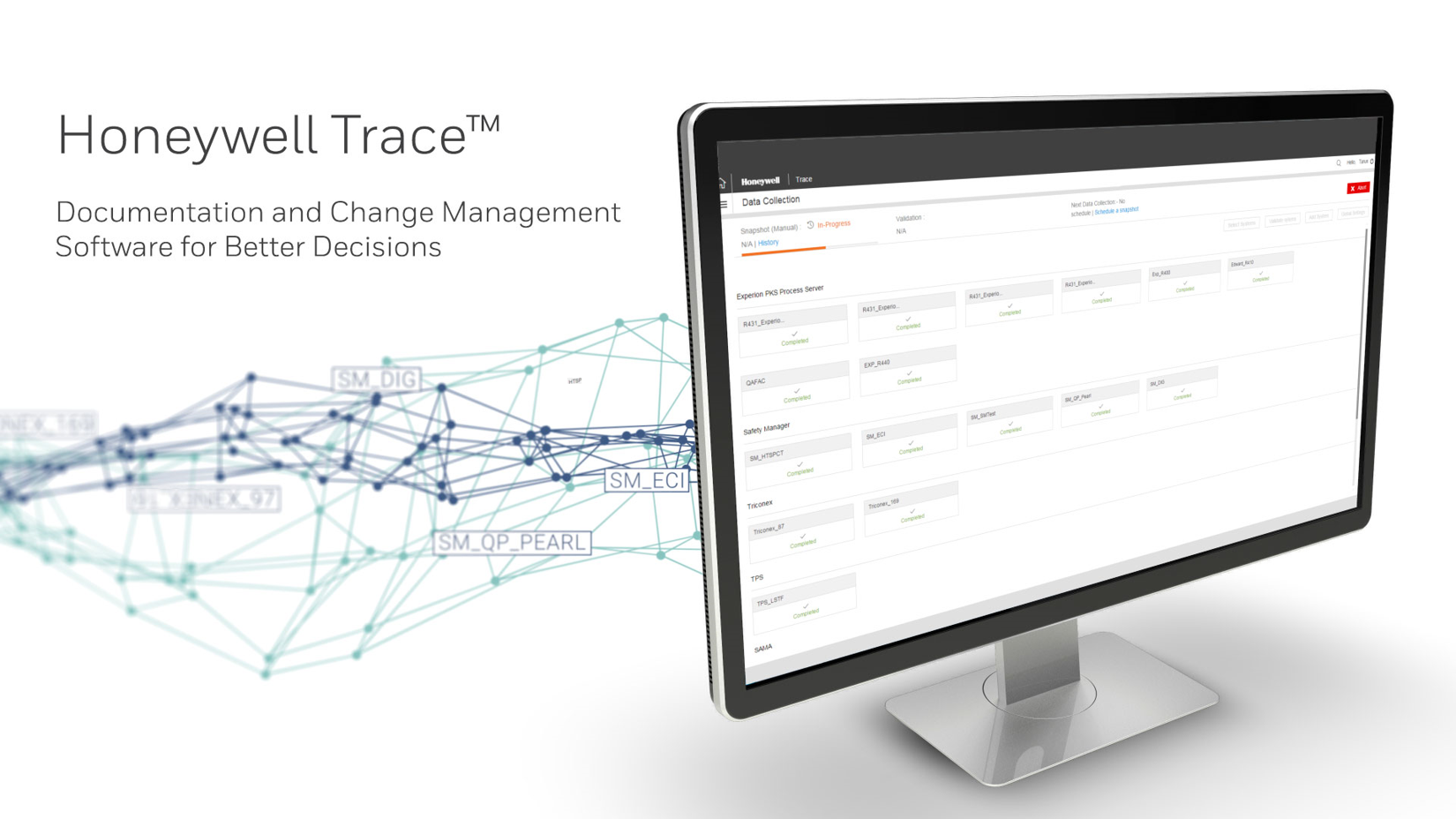
Honeywell Process Solutions (HPS) today announced the introduction of documentation and change management software that will help its customers’ industrial control system integrity. Honeywell Trace replaces paper-based records and spreadsheets with an automated solution. This helps minimize errors due to changes in configurations, improve worker productivity, and simplify automation asset management by providing a single integrated view of complex system interactions.
Around the world, many process industry organizations need to meet critical management of change (MOC) challenges within their operations. In particular, plant owners/operators need to know who is interacting with control systems and when changes have been made. They also require a clear understanding of configuration anomalies.
“Driven by the growth of our outcome-based programs and a commitment that all processes and tools deliver more efficient service, it is critical that we have the ability to quickly collect and accurately report on system information, configuration history and performance conditions,” said John Rudolph, vice president and general manager, HPS Lifecycle Solutions and Services. “Honeywell Trace responds to these key requirements, providing critical data that lets users know what, when, and why actions were taken and how they compare to actions in the past. The precision and comprehensiveness of its change analysis can reduce several days of manual effort.”
Honeywell Trace is a sophisticated data collection solution that helps expand the visibility of control configurations while automating the documentation of traditional tribal knowledge and actions taken by plant personnel. These improvements will enable companies to enhance regulatory compliance, reduce configuration errors, spend less time in project planning, and minimize troubleshooting and forensics effort.
“Honeywell customers employing the Trace solution can expect a substantial reduction in manual troubleshooting, reduced quality assurance and factory acceptance test (FAT) project activities, and dramatically faster data collection,” Rudolph said.
Honeywell Trace enables plant managers, safety managers, engineers and others to see how the facility is divided and view changes that have occurred to a group of components over collected snapshots. Operations can continue as usual during data snapshots, as the software does not impact the engineering system during collection periods. Personnel can learn how changes impact performance through system health reports, better understand data flows and logic, and avoid problems during maintenance.
Trace makes it easy to identify and assign hardware statuses, reserve hardware, and improve project planning with I/O channel spare management. Engineering teams are able to maintain their network and hardware topology without having to redraw it every time a change is made. Honeywell Trace allows for better decision-making and ultimately improves operational effectiveness.
The new software documents data up to 300 times more frequently than other MOC tools and provides the most powerful search and parameter query functions. It offers smart change analysis, user-configurable defect definition capabilities, real-time system performance assessments, and an intuitive user experience design with dashboards and logical network views.

by Gary Mintchell | Mar 15, 2017 | Automation, Process Control, Standards
The latest attempt at building an open control platform is driven by ExxonMobil and given some support by the ARC Advisory Group by offering a venue for meetings. I wrote about the meeting during the ARC Forum in Orlando. What I find most interesting is linking this to the Internet of Things.
It will be interesting to see where this leads. I’ve seen attempts in the past to try to get suppliers to ditch their computing or control platforms to go with a generic open system where end users could drive pricing down to commodity levels. Of course, such a system would require lots of engineering—a boon to systems integrators.
Although the dream of complete plug-and-play requiring no integration is a problem waiting a solution. We’ve seen this scenario play out in the computer business. The result was locked down hardware with a measure of interoperability of systems. I think that this is where standards are most valuable.
WindRiver has cast its lot with the ExxonMobil-led Open Process Control initiative and has announced a product in support of the effort. It has announced availability of a software virtualization platform enabling critical infrastructure companies to cost-effectively evolve aging legacy control systems not previously designed to support the connected nature of IoT. Wind River Titanium Control empowers the next generation of on-premise analytics to optimize industrial processes.

“ARC believes the influx of new IIoT technologies now entering the automation market has the potential to be a major disruption to existing business models that have been relatively stable for decades,” said Harry Forbes, research director at ARC Advisory Group, a leading technology research firm for industry and infrastructure. “An excellent example is Titanium Control, which combines Wind River’s long experience in real-time operating systems with on-premise cloud computing technology. This combination enables the virtualization of real-time automation applications that until recently could only be implemented in embedded systems hardware. The implications of this capability for the manufacturing automation market are very far-reaching, and automation suppliers are noticing.”
Because traditional industrial control systems were not designed to support IoT, most are rigid, single purpose, and have a high cost to deploy, integrate, and maintain. Additionally, the obsolescence cycle is driving system updates that require new systems to keep pace with innovation while maintaining or lowering capital costs.
Titanium Control is a commercially deployable on-premise cloud infrastructure that virtualizes traditional physical subsystems using a platform based on open standards. It delivers the high performance, high availability, flexibility, and low latency needed to reduce capital and operating expenses, as well as minimize unscheduled downtime for industrial applications and control services at any scale. Unlike enterprise IT virtualization platforms, it provides high reliability for applications and services deployed at the network edge, for example in fog deployments.
Key features of Titanium Control include:
- De facto standard open source software for on-premise cloud and virtualization, including Linux, real-time Kernel-based Virtual Machine (KVM) and OpenStack
- High performance and high availability with accelerated vSwitch and inter-VM communication, plus virtual infrastructure management
- Security features including isolation, secure boot and Trusted Platform Module enabled through Enhanced Platform Awareness
- Scalability from two to over 100 compute nodes
- Hitless software updates and patching with no interruption to services or applications
“With the emergence of Industrial IoT, companies are looking to deploy next-generation open and secure control systems; Titanium Control addresses this need, and is in active trials with customers in industries ranging from manufacturing to energy to healthcare,” said Jim Douglas, president of Wind River. “Our software has been providing these companies with powerful ways to increase efficiency and bolster safety, security, and reliability for the last 35 years. With the addition of Titanium Control to our product portfolio, Wind River is driving a new industrial era through virtualization, real-time performance and edge-to-cloud connectivity.”
Titanium Control is part of the Wind River Titanium Cloud portfolio of virtualization products for the deployment of critical services from operations to data center environments that require real-time performance and continuous service availability. It is optimized for Intel Xeon processors, and is pre-validated on hardware from the leading providers of Intel-based servers.

by Gary Mintchell | Feb 16, 2017 | Security
 Cyber security was a pervasive topic at the recent ARC Forum in Orlando. There were at least five suppliers with exhibits featuring security. Several were startups headed by former Israeli security officers. Guess they should know what they’re doing.
Cyber security was a pervasive topic at the recent ARC Forum in Orlando. There were at least five suppliers with exhibits featuring security. Several were startups headed by former Israeli security officers. Guess they should know what they’re doing.
Featured:
Bedrock Automation
Claroty / Rockwell Automation
Indegy
PAS
Nazomi
Bedrock Automation
Bedrock Automation announced newly upgraded control system firmware that extends its intrinsic cyber security protection to networks, the Industrial Internet of Things (IIoT) and third-party applications. Bedrock Cybershield 2.0 firmware not only enables authentication and encryption of I/O networks and field devices, it now protects compliant networks and user applications such as controller configuration, engineering and SCADA. It achieves this with the world’s first industrial control system (ICS) certification authority (CA) – drawing on the power and flexibility of public key infrastructure (PKI) and Transport Layer Security (TLS).
Bedrock Automation also announced a controller that enables end users to obtain customized, company specific root keys With the inclusion of more than 40 intrinsic technologies, the BedrockOpen Secure Automation (OSA) platform initially delivered on two fundamentals of cyber defense: a secure control platform and secure component supply chain. The resulting endpoint root of trust leverages hardware-based secret root keys and certificates for advanced cryptographic authentication of Bedrock hardware and software components, which are further fortified with layers of anti-tamper protection.
“Our first objective was to deliver a hardware-based endpoint root of trust, which we did with the Cybershield 1.0, which was built into last year’s product release. Cybershield 2.0 is our next giant leap. It validates our built-in versus bolted-on technologies and is forward and backward compatible. This 2.0 firmware upgrade demonstrates how we continuously enhance intrinsic defense and lead the digital convergence of OT cyber security with enterprise class technologie,” said Bedrock founder, CTO and VP Engineering Albert Rooyakkers.
Claroty
Industrial security software provider Claroty and Rockwell Automation will work together to combine their security products and services into future, packaged security offerings.
After a competitive review process, Rockwell Automation selected Claroty for the company’s anomaly-detection software purpose built for industrial network security. The software creates a detailed inventory of an end user’s industrial network assets, monitors traffic between those assets, and analyzes communications at their deepest level. Detected anomalies are reported to plant and security personnel with actionable insights to help enable efficient investigation, response and recovery.
“More connected control systems combined with the potential for more attacks on those systems have made cybersecurity a top concern in the industrial world,” said Scott Lapcewich, vice president and general manager, Customer Support and Maintenance, Rockwell Automation. “Claroty’s deep-visibility software platform and expertise in industrial security made the company a natural fit for substantial collaboration as we grow our existing portfolio of security service and support offerings.”
A key characteristic of the Claroty software is its ability to explore the deepest level of industrial network protocols without adversely impacting the system. This enables end users to identify even the smallest anomalies while protecting complex and sensitive industrial networks. Traditional IT security software often uses active queries and requires a footprint on the network, which can ultimately disrupt operations. However, the Claroty platform uses a passive-monitoring approach to safely inspect traffic without the risk of disruption.
“The Claroty platform can detect a bad actor’s activities at any stage, whether they’re trying to gain a foothold on a network, conduct reconnaissance or inflict damage,” said Amir Zilberstein, co-founder and CEO, Claroty. “It also can detect human errors and other process integrity issues, which are often more common than threats from bad-actors. For example, the software monitors for critical asset changes that, if done incorrectly, could result in unexpected downtime. The system also identifies network-configuration issues that could expose a system to outside threats.” here.
Indegy
Last year I wrote about Indegy as a stealth security startup. This year, not so much stealth. It was one of several at the Forum. They told me this year that they are more OT focused than IT focused. Most of the other companies look at network traffic trying to find anomalies. Indegy focuses on changes in the PLC. The founders are from Israeli security plus retired US General Petratis is on the board.
PAS
PAS is not a new company. It has been known as the “human reliability” company focused on its background in alarm management expanded into cataloging process control systems for purposes of change management. It has taken these technologies to the next level by applying them to cyber security. Over the past two years, PAS has invested heavily in people and technology to become a leading process cyber security company.
Nozomi
Nozomi, a Swiss company, began on the offensive side of cyber security. Founders have an academic background. It switched to the defensive side with a tool that exposes visibility in a process system. Its second co-founder brings a background of machine learning to the mix. The technology listens to the network with an understanding of the process and detects anomalies.

by Gary Mintchell | Nov 15, 2016 | Automation, Security
 Cyber protection takes on a number of forms. Most everything involves “defense in depth” strategies. I just talked with an Israeli company started by former security agents who has found a different vulnerability and counteracts it. This is the first of three press releases I’ve been sitting on for release today. I guess Nov. 15 is a magic day in the PR world.
Cyber protection takes on a number of forms. Most everything involves “defense in depth” strategies. I just talked with an Israeli company started by former security agents who has found a different vulnerability and counteracts it. This is the first of three press releases I’ve been sitting on for release today. I guess Nov. 15 is a magic day in the PR world.
APERIO Systems emerged from stealth mode, launching the industry’s first technology that detects artificial manipulations of industrial process data, enabling operators to take real-time corrective action without service disruption to industrial control systems (ICS). From the rate of gas flow at a petroleum refinery, to the temperature and spin rates of turbines in a power plant, or the chlorine level of water supply networks, APERIO Systems’ proprietary Data Forgery Protection (DFP) technology delivers the last line of defense in protecting critical SCADA systems against insider and external threats.
APERIO Systems, already deployed at several sites across EMEA, secured seed funding from a consortium of private investors, including prominent cybersecurity veterans Doron Bergerbest-Eilon, Liran Tancman, and Shlomi Boutnaru. Bergerbest-Eilon is renowned for his role in establishing the agency charged with protecting all critical infrastructure in the State of Israel and is the former director of the security and protection division of the Israel Security Agency (ISA). He is currently the founder, president and CEO of ASERO Worldwide, a security consulting firm. Tancman and Boutnaru, who played key roles in building Israel’s cybersecurity capabilities, founded predictive cybersecurity startup CyActive, which was acquired by PayPal in 2015.
“Current solutions focus on keeping hackers outside critical systems, but attacks like the one that took down the power grid in Ukraine clearly show that sophisticated attackers will eventually penetrate these systems,” said Bergerbest-Eilon. “Once attackers breach a system, they must blind the operators and protection mechanisms by falsifying data in order to inflict severe and long-lasting damage. This entirely new category of Data Forgery Protection (DFP) is the key to keeping our critical infrastructure safe from attacks.”
Industrial control systems (ICS) are generally outdated from a cybersecurity perspective, vulnerable and difficult to patch because mission critical systems cannot be taken offline. While the threat to ICS is growing, critical systems security products on the market today are intrusive, hard to maintain, costly to integrate, and often produce vague and unactionable alerts, which cannot be acted upon by critical utility control rooms.
“Think of APERIO Systems as a polygraph for process data — it detects when your system is lying to you,” said Yevgeni Nogin, CEO of APERIO Systems. “With the unrelenting tenacity of cybercriminals, critical infrastructure breaches are inevitable. By guaranteeing the authenticity and integrity of operational data, APERIO Systems ensures that operators always know what’s really going on, enabling them to react quickly to a breach and take corrective action — making the critical systems resilient to the most dangerous of attacks.”
APERIO Systems’ advanced proprietary algorithms search for the data’s unique fingerprints and validate its authenticity. Any mismatches generate an alert and APERIO Systems pinpoints the attacked equipment and forged process data. Using a sophisticated combination of physics and state-of-the-art machine learning techniques, APERIO Systems reconstructs the real values of the forged operational data and reverts it to its original state in real time — establishing unprecedented operational resilience.
How APERIO Systems Protects
Both internal and external attackers can penetrate the most critical infrastructures, causing severe and long lasting damage. In order to do so, they must hide their malicious activity and deceive plant operators by forging the reported values of critical devices — remaining undetected and preventing timely corrective action. APERIO Systems’ Data Forgery Protection technology immediately exposes forged system readings to safeguard critical control systems and allow quick and effective remediation.
- APERIO Systems provides:
Data Forgery Protection (DFP): Validates integrity and authenticity of reported signals to provide operators with true state awareness, enabling them to take corrective action in real time.
- Process Continuity: Enables trust in the most critical data and provides resilience when attacked.
- Operational Alerts: Fast, actionable, specific and accurate alerts integrate cybersecurity into operational emergency procedures, allowing operators to mitigate permanent damage.
- Accurate and Relevant: Alerts operators only when the reported process state does not reflect the plant’s real situation — providing an extremely low false alert rate.
- Minimized Risk: Passive and non-intrusive system minimizes operational risks, as well as installation and maintenance costs.
- Counters Insider Threats: Protects the plant’s process continuity from both external and internal actors.
APERIO Systems is led by a veteran executive team with roots in the elite units of the Israel Defense Forces (IDF), as well as top cybersecurity and industrial companies:
- Yevgeni Nogin, CEO — a graduate of the elite “Talpiot” IDF military academy served over nine years in elite intelligence and R&D units of the IDF, and brings expertise in SCADA systems security.
- Michael Shalyt, VP Product — a graduate of the “Psagot” IDF academic program and served as leading researcher and team leader in the elite 8200 unit. Prior to joining APERIO Systems, he led the malware research team at Check Point.
- Itay Baruchi, Head of Algorithms — served as director of Industrial MRI, where he worked closely with several of the biggest oil and gas drilling companies. Before that, he founded and served as CTO of Pythagoras Solar.
- Charles Tresser, Chief Scientific Officer — a world renowned expert in dynamical systems. Tresser is one of the world’s leading experts in chaos theory and formerly Director of Research at IBM and France’s National Center for Scientific Research (CNRS).

by Gary Mintchell | Dec 7, 2015 | Automation, News, Security
 SCADA devices and networks remain a prime target for cyber attacks. Everything I’ve written has approached cybersecurity from a different angle. This is the first solution that has come my way that uses a deception approach.
SCADA devices and networks remain a prime target for cyber attacks. Everything I’ve written has approached cybersecurity from a different angle. This is the first solution that has come my way that uses a deception approach.
Attivo Networks announced Dec. 7, 2015 a release of its deception-based Attivo BOTsink solution that provides continuous threat detection on Industrial Control Systems (ICS) SCADA devices used to monitor and control most manufacturing operations as well as critical infrastructure such as natural gas, oil, water, and electric power distribution and transmission systems around the world. Cyberattacks on these targets can and have resulted in disruption of critical local, regional, and national government and commercial infrastructures. As a result, when they are breached, the impact on societies they serve stands to be catastrophic.
According to a study by the Pew Internet and American Life Project, 60 percent of the technology experts interviewed believe that a major cyberattack will happen. The damages to property and ensuing theft will amount tens of billions of dollars, and the loss of life will be significant.
Scalable SCADA protection
“We are proud to be the first in the industry to provide customers a globally scalable, deception-based threat detection solution for SCADA protection,” emphasizes Tushar Kothari, CEO of Attivo Networks. “Many of our customers from the energy industry have requested the extension of our Attivo Deception Platform into their production and manufacturing control networks so they can get real-time visibility and the ability to promptly identify and remediate infected devices. As one stated, ‘a breach on those networks can be catastrophic and Attivo wants to do everything we can to prevent a disaster or risk to lives.”
SCADA systems had originally been designed to monitor critical production processes without consideration to security consequences. Security had been generally handled by keeping the devices off the network and the Internet using “air gaps” where malware could only be transmitted by the thumb drives used by technicians. However, today vulnerable SCADA systems are increasingly being connected to the corporate IT infrastructure and Internet, making them easily accessible to a remote attacker.
Examples of this would be the Sandworm malware that attacked Telecommunications and Energy sectors, Havex malware that infected a SCADA system manufacturer, and BlackEnergy malware that attacks ICS products manufactured by GE, Siemens, and Advantech. These attacks primarily targeted the operational capabilities of these facilities. With the increased malicious and sophistication of malware, concerns are now escalating to fears of an irreversible disaster.
Situational awareness
“Industrial systems have increasingly come under scrutiny from both attackers and defenders,” said Chris Blask, Chair of the Industrial Control System Information Sharing and Analysis Center (ICS-ISAC). “Situational awareness is the focus of the ICS-ISAC and its membership, including the ability for asset owners to detect and respond to incidents on their systems.”
These devices generally have long lifecycles creating an exposed environment driven by equipment that is less hardened and patches made infrequently. Additionally, because of their critical functions, SCADA devices cannot be taken offline frequently or for any length of time. This, along with costs that can run into the millions for every hour the network is offline, has made patching very difficult, often as infrequent as once a year, leaving many industrial facilities open to attacks. These risks are quite large considering these devices are found everywhere in electrical facilities, food processing, manufacturing, on-board ships, transportations and more.
“Companies operating in critical infrastructures like energy, utilities, nuclear, oil and gas know that they are not only vulnerable to the same security issues faced by most enterprises, they have the added enticement as a rich target for cyber terrorism,” stated Tony Dao, Director Information Technology, Aspect Engineering Group. “They recognize that securing their industrial control processes is not only critical to them, but to the institutions they serve. A loss would not only have repercussions throughout their economic sector but throughout the entire economy.”
The vulnerabilities begin with the use of default passwords, hard-coded encryption keys, and a lack of firmware updates, which pave the way for attackers to gain access and take control of industrial devices. Traditional perimeter-based solutions are designed to detect attacks on these devices by looking for suspicious attack behavior based on known signature patterns. SCADA supervisory systems are computers running normal Windows operating systems and are susceptible to zero day attacks, in which there are no known signatures or software patches. Several vulnerabilities also exist in the standard and proprietary protocols within Logic Controllers. Popular protocols include MODBUS (supervision and control), DNP3 (Energy and Water), BACNET (Building Automation), and IPMI (Baseboard Management Control).
Deception technology
Attivo Networks takes a different approach to detecting cyber attacks on ICS- SCADA devices. Instead of relying on signatures or known attack patterns, Attivo uses deception technology to lure the attackers to a BOTsink engagement device. Customers have the flexibility to install their own Open Platform Communications (OPC) software while running popular protocols and PLC devices on the BOTsink solution making it indistinguishable from production SCADA devices. This provides real-time detection of BOTs and advanced persistent threats (APTs) that are conducting reconnaissance to mount their attacks on critical facility and energy networks. Additionally, BOTsink forensics capture information including new device connections, issued commands and connection termination, enabling administrators to study the attacker’s tools, techniques, and information on infected devices that need remediation.
The Attivo SCADA solution is provided through a custom software image that runs on its BOTsink appliance or virtual machine. SCADA BOTsink deployment and management are provided through the Attivo Central Manager, which provides global central device management and threat intelligence dashboards and reporting.
“To a significant degree, the growing security problems impacting industrial control systems have originated from the fact that ICSs are increasingly less and less isolated from outside networks and systems, and ICSs are now more susceptible and vulnerable to attacks,” comments Ruggero Contu, Research Director at Gartner in his Market Trends: Industrial Control System Security, 2015 report. “At the heart of this change is the demand to integrate enterprise IT systems to operational technology, and for remote connectivity.”
Check out this whiter paper. Dynamic Deception for Industrial Automation and Control Systems






 Cyber security was a pervasive topic at the recent ARC Forum in Orlando. There were at least five suppliers with exhibits featuring security. Several were startups headed by former Israeli security officers. Guess they should know what they’re doing.
Cyber security was a pervasive topic at the recent ARC Forum in Orlando. There were at least five suppliers with exhibits featuring security. Several were startups headed by former Israeli security officers. Guess they should know what they’re doing.




