
by Gary Mintchell | Dec 10, 2019 | Commentary, Internet of Things, Manufacturing IT, Operations Management
Top Tens and Top Twenties of the past or future year have never been my favorites. However, one can perceive trends and strain out little nuggets of gold by scanning several. Especially industrial taken broadly along with Internet of Things (IoT) and other current digital trends. I just had an interesting chat with Sean Riley, Global Director of Manufacturing and Transportation for Software AG, who released his Top Ten for 2020.
Following are his ideas interspersed with a few of my comments.
Cost Management Becomes Exceptional
As uncertainty enters the global manufacturing outlook, enterprises will become myopically focused on cost reductions. This will drive organizations to find more efficient methods of providing IT support, leveraging supplier ecosystems and simplifying value chains. [GM-much of my early work was in cost management/reduction; this is a never-ending challenge in manufacturing; however, tools continue to evolve giving us more and better solutions.]
A Blurred Line Between Products & Services
Manufacturers continue their product innovation quest and more manufacturers will begin focusing on how to deliver products as a service. The Manufacturers that have already created smart products and have elevated service levels will now begin to work out the financing considerations needed to shift from a sales based to a usage based revenue model. [GM-This is a trend most likely still in its infancy, or maybe toddler-hood; we see new examples sprouting monthly.]
Moving To Redefine Cost Models To Match Future Revenue Streams
Anticipating the shift to continual revenue streams, manufacturers will seek to shift costs to be incurred in a similar manner. This will be initially seen as a continued push to subscription based IT applications. While much progress has already been made, a larger focus will occur. [GM-I like his idea here of balancing capital versus expense budgets, continually finding the best fund source for shifting costs.]
IT Focuses on Rapid Support for Growth
The lines between business and IT users become blurred as no-code applications allow for business users to create integration services. IT professionals will leverage DevOps & Agile methodologies alongside of microservices and containers to rapidly develop applications that are able to generate incremental growth as requested by business users. This will be critical to the near term success for manufacturers, especially with economic headwinds that seem to be growing stronger. [GM-I didn’t ask about DevOps, but this idea is springing into the industrial space; cloud and software-as-a-service provide scalability both up and down for IT to balance costs and services.]
Industrial Self-Service Analytics Become Mission Critical
Industrie 4.0 / Smart Manufacturing initiatives continue to receive greater amounts of investment but in the near term, manufacturers will focus on unleashing the power of the data they already have. Historians, LIMS, CMMS’ have valuable data going to and in them and enabling production engineers to leverage that data rapidly is critical. Industrial Self-Service Analytics that allow production and maintenance professionals to leverage predictive analytics without IT assistance will sought as a powerful differentiating factor. [GM-we are beginning to see some cool no-programming tools to help managers get data access more quickly.]
Industrie 4.0 / Smart Manufacturing Initiatives Continue to Draw Investment
It’s no surprise that Manufacturers will continue to invest in Industrie 4.0 as the promises are great however, the scaled returns have not been realized and won’t be realized in the near term. The difficult of implementing these initiatives has surpassed manufacturers expectations for several reasons. First, traditional OT companies were trusted to deliver exceptional, open platforms and that wasn’t delivered. Secondly, collaboration efforts between IT & OT professionals proved to be more convoluted and difficult than expected. [GM-I’m thinking these ideas became overblown and complex, and that is not a good thing; to swallow the whole enchilada causes stomach pain.]
Artificial Intelligence Enters the Mix
AI won’t allow for users to sit back and relax while AI handles all of their tasks for them but it will make an appearance in back office tasks. Freight payment auditing, invoice payment and, in some select areas, chatbots will be the initial main stream uses of AI and will be seen as not becoming an anomaly but be understood to be more mainstream this year. [GM-I think still an idea looking for a problem; however some AI ideas are finding homes a little at a time.]
3D Printing Find New Uses
While this technology has steadily crept into production lines, the push towards usage based product pricing will have the technology move into after market services. Slow moving parts will be the first target for this technology which will help to free up much needed working capital to support financial transformation. [GM-watch for better machines holding tighter tolerances making the technology more useful.]
5G & Edge Analytics Enable New Possibilities
As Industrie 4.0 is continued to be pursued, Manufacturers will implement new initiatives that could not previously be realized without the high speed data transmission promises of 5G or the ability to conduct advanced analytics at the edge where production occurs. This will also provide manufacturers with new methods to securely implement Smart Manufacturing initiatives and in new locations that were not previously feasible due to connectivity issues. [GM-5G is still pretty much a dream, but there is great potential for some day.]
Security Still Remains a Critical Focus
With the increasing rate of IoT sensors, IT-OT convergence, the usage of API’s and the interconnectivity of ecosystems ensuring data security remains a top priority for manufacturers. As more data becomes more available, the need to increase levels of security becomes ever greater. [GM-ah, yes, security–a never-ending problem.]

by Gary Mintchell | Dec 6, 2019 | Internet of Things, Networking, Wireless
Suddenly the wireless networking side of IoT connectivity is hitting my radar. Since the culmination of the “wireless wars” of 10 years ago, this technology/market area has settled into supplying usable products. This information came from Honeywell—In short, by supplying ISA100 Wireless and WirelessHART connectivity to Cisco’s next-generation Wi-Fi Access Point, Honeywell’s OneWireless IoT Module can help users increase industrial plant productivity, worker safety, and digital transformation readiness.
Honeywell is developing a OneWireless IoT Module for the next-generation of Cisco’s industrial access points, the Cisco Catalyst IW6300 Heavy Duty Series Access Point. The Honeywell and Cisco technologies will form the backbone of Honeywell’s OneWireless Network.
The joint wireless solution enables Honeywell customers to quickly and easily deploy wireless technologies as an extension of their Experion Process Knowledge System (PKS). Combining the leading IT network technology by from Cisco and the leading Honeywell OneWireless multi-protocol technology provides customers with a single infrastructure that meets all their industrial wireless needs.
“For the past decade, Cisco and Honeywell have worked together to deliver secure, wireless solutions to connect mobile workers and field instrumentation in the most challenging process manufacturing environments,” said Liz Centoni, senior vice president and general manager, Cisco IoT. “We’ve had great success in bringing IT and operational teams together to reduce complexity and improve efficiency. Now, we are building on that foundation to extend the power of intent-based networking to the IoT edge.”
When combined with the Honeywell OneWireless IoT Module, the Cisco Catalyst IW6300 Heavy Duty Series Access Point offers the security, speed, and network performance needed to allow the seamless extension of the process control network into the field.
“The OneWireless IoT Module is Honeywell’s latest innovation as a leader in wireless technology,” said Diederik Mols, business director Industrial Wireless, Honeywell Process Solutions. “Our customers will benefit from OneWireless functioning as a seamless extension of Experion PKS and simplified deployment made possible by integrating the IoT module and aerials into a single unit.”

by Gary Mintchell | Aug 8, 2019 | Internet of Things, Manufacturing IT
The spread of connected devices with the resultant flow of data throughout the industrial enterprise spurs concern for security and trustworthiness of that data. The Industrial Internet Consortium (IIC) and its members recognize this problem / challenge.
I normally have a conversation with the authors of the IIC papers to get a context and sense of all the work involved in their development. In this particular case, I ran out of time. Many of you know that I am up to my eyes in soccer activities at this time of year. I just finished leading a class of new referees while I am at one of my peak times for assigning referees to games. Sometimes, I just don’t have enough hours. I bet you have never felt that…
So, IIC has published the Managing and Assessing Trustworthiness for IIoT in Practice white paper. The paper serves as an introductory guide to trustworthiness in IIoT, which is driven by the convergence of IT with OT, and includes a definition of trustworthiness, examples and a best-practice approach to managing trustworthiness in IIoT systems.
Confidence is essential to business, including confidence that the consequences of decisions and processes are acceptable and that business information is handled properly. The advent of IIoT means that confidence is also now required in technologies, physical components, and systems in addition to confidence in individuals, organizations and processes.
“The fact is that it is possible to have ‘too much’ trustworthiness,” said Jim Morrish, co-Chair of the IIC Business Strategy and Solution Lifecycle Working Group. “Trustworthiness costs, in terms of the costs of devices and associated software, and also often in terms of user experience and functionality. A trustworthiness solution for a nuclear processing plant would be an unnecessary hindrance to the day-to-day operations of a peanut butter manufacturer.”
The white paper’s best-practice approach to managing trustworthiness is comprised of four phases: baselining the system, analyzing potential trustworthiness events, implementing trustworthiness targets and governance, and iterating and maintaining the resulting trustworthiness model.
“This whitepaper demonstrates that trustworthiness is more than just another academic phrase to describe expectations of stakeholders, operators and users of an IIoT system,” said Marcellus Buchheit, President and CEO of Wibu-Systems USA, cofounder of Wibu-Systems AG in Germany and co-chair of the IIC Trustworthiness Task Group. “This paper presents several models that show how trustworthiness can be practically used in business decisions to increase trust in an IIoT system under the impact of business reality and constraints.”
The white paper also highlights that trustworthiness is not a static concept. “An IIoT system must address trustworthiness requirements throughout the lifecycle of the system. This means that industrial IoT trustworthiness is not a project with a finite start and a finite end. It is a journey that must be powered by an established program,” said Bassam Zarkout, founder of IGnPower and co-author of the paper.
“Security is already recognized as one of the most important considerations when designing an IIoT system,” said Frederick Hirsch who is a Standards Manager at Fujitsu, and also co-chair of the IIC Trustworthiness Task Group. “This white paper expands on that thinking by recognizing that safety, privacy, reliability and resilience need to be considered in conjunction with security to establish trust that IIoT systems will not only be functional but also will not harm people, the environment or society.”
The white paper discusses a live example of an IIoT system analysed from a trustworthiness perspective. Fujitsu’s Factory Operation Visibility & Intelligence (FOVI) system (and IIC testbed) has the primary goal of bringing more visibility of operations to plant managers in near-real time. The goal is to reduce human errors, bring more predictability to product assembly and delivery, and optimize production all while ensuring a sufficient level of trustworthiness.
“FOVI highlights how the different aspects of trustworthiness can impact business performance,” said Jacques Durand, Director of Engineering and Standards at Fujitsu, co-Chair of the IIC Business Strategy and Solution Lifecycle Working Group and also a member of the IIC Steering Committee. “For instance slowing down a production line can reduce costs associated with stress on machinery and machine operators, but such a course of action may also adversely impact productivity or lead time. In the white paper we highlight the need to understand trade-offs and to use metrics in a data-driven and intelligent manner.”
The Managing and Assessing Trustworthiness for IIoT in Practice white paper sets the stage for further work that the IIC will undertake focusing on trustworthiness.
The full IIC Managing and Assessing Trustworthiness for IIoT in Practice white paper and a list of IIC members who contributed can be found on the IIC website.

by Gary Mintchell | Nov 16, 2018 | Automation, Security
I didn’t attend Automation Fair this year, but I have been watching for news. Here is a first product release from Rockwell Automation using CIP Security—an extension of the Common Industrial Protocol promulgated by ODVA designed for, well, secure communication as one part of a defense-in-depth strategy.
CIP is the application-layer protocol for EtherNet/IP. CIP Security supports transport layer security (TLS), the most proven security standard in widespread use on the World Wide Web today.
“CIP Security can protect devices and systems that use EtherNet/IP from some of the top risks in connected operations, such as unauthorized PCs,” said Tony Baker, portfolio manager, security, for Rockwell Automation. “It does this in a few key ways. First, it limits device connectivity to only trusted PCs and devices. It also guards against packet tampering to protect data integrity. Finally, it encrypts communications to avert unwanted data reading and disclosure.”
Engineers will be able to implement CIP Security in their systems through new Rockwell Automation products and firmware updates to existing products such as Allen-Bradley ControlLogix controllers, communication modules, and Kinetix servo drives.
In addition, the newly enhanced FactoryTalk Linx communications software allows FactoryTalk visualization and information software running on a PC to communicate to CIP Security-enabled devices. The new FactoryTalk Policy Manager tool within the FactoryTalk software is used to implement and configure security policies between CIP Security-enabled devices.
Rockwell Automation developed this new capability to work with existing industrial control devices regardless of whether or not they were designed to support CIP Security. This allows industrial users to phase in security over time and retrofit existing installations.
In addition, Allen-Bradley ControlLogix 5580 controllers will soon be certified compliant with the IEC 62443-4-2 security standard, building on the IEC 62443-4-1 certification that the Rockwell Automation Security Development Lifecycle has already received.
This latest certification means the controllers will meet the global standard’s robust cybersecurity requirements to help companies secure their connected operations. The ControlLogix 5580 family of controllers is one of the first platforms on the market to achieve this compliance.

by Gary Mintchell | Aug 24, 2018 | Automation, Operator Interface, Technology, Workforce
Simulators are great training tools. It sure beats flying 777s around for your annual pilot recert. Gaming technology has become so good along with many other technologies, that operators of process plants and machinery should be well trained to respond appropriately to any emergency.
Georgia Institute of Technology sent this information about an advancement in simulation for operator training. Good stuff.
A simulator that comes complete with a virtual explosion could help the operators of chemical processing plants – and other industrial facilities – learn to detect attacks by hackers bent on causing mayhem. The simulator will also help students and researchers understand better the security issues of industrial control systems.
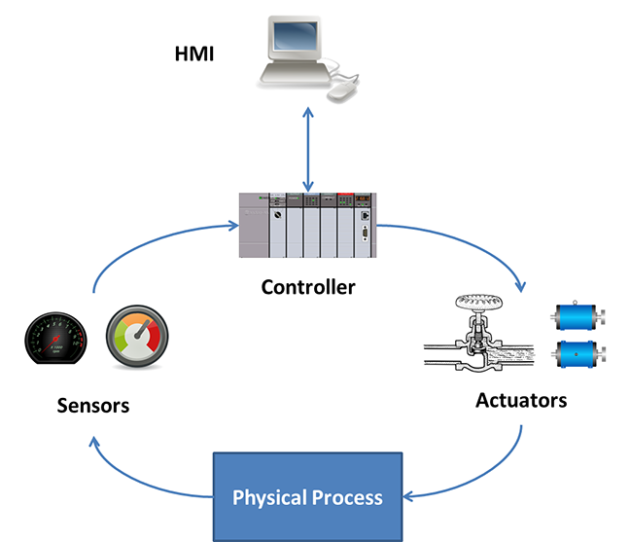
This flow chart shows data flows within a simulated chemical processing facility.
Facilities such as electric power networks, manufacturing operations and water purification plants are among the potential targets for malicious actors because they use programmable logic controllers (PLCs) to open and close valves, redirect electricity flows and manage large pieces of machinery. Efforts are underway to secure these facilities, and helping operators become more skilled at detecting potential attacks is a key part of improving security.
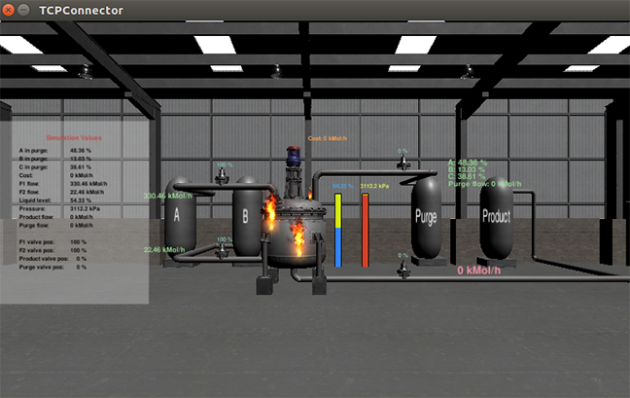
Screen captures show a simulated explosion in a chemical processing plant precipitated by a cyberattack on the system.
“The goal is to give operators, researchers and students experience with attacking systems, detecting attacks and also seeing the consequences of manipulating the physical processes in these systems,” said Raheem Beyah, the Motorola Foundation Professor in the School of Electrical and Computer Engineering at the Georgia Institute of Technology. “This system allows operators to learn what kinds of things will happen. Our goal is to make sure the good guys get this experience so they can respond appropriately.”
Details of the simulator were presented August 8 at Black Hat USA 2018, and August 13 at the 2018 USENIX Workshop on Advances in Security Education. The simulator was developed in part by Atlanta security startup company Fortiphyd Logic, and supported by the Georgia Research Alliance.
The simulated chemical processing plant, known as the Graphical Realism Framework for Industrial Control Simulations (GRFICS), allows users to play the roles of both attackers and defenders – with separate views provided. The attackers might take control of valves in the plant to build up pressure in a reaction vessel to cause an explosion. The defenders have to watch for signs of attack and make sure security systems remain operational.
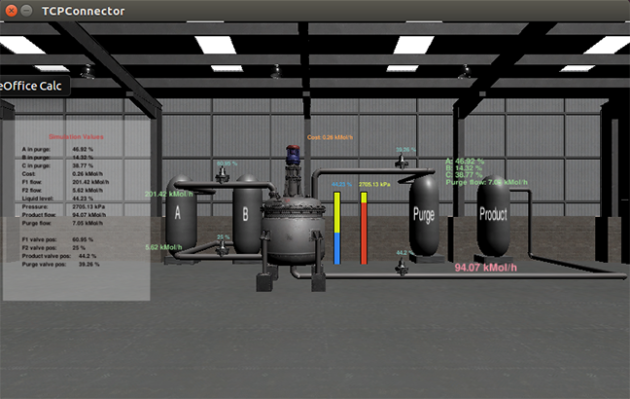
Screen capture shows a chemical processing plant in which critical parameters are rising due to false process data and control commands injected by an attacker.
Of great concern is the “man-in-the-middle” attack in which a bad actor breaks into the facility’s control system – and also takes control of the sensors and instruments that provide feedback to the operators. By gaining control of sensors and valve position indicators, the attacker could send false readings that would reassure the operators – while the damage proceeded.
“The pressure and reactant levels could be made to seem normal to the operators, while the pressure is building toward a dangerous point,” Beyah said. Though the readings may appear normal, however, a knowledgeable operator might still detect clues that the system has been attacked. “The more the operators know the process, the harder it will be to fool them,” he said.
The GRFICS system was built using an existing chemical processing plant simulator, as well as a 3D video gaming engine running on Linux virtual machines. At its heart is the software that runs PLCs, which can be changed out to represent different types of controllers appropriate to a range of facilities. The human-machine interface can also be altered as needed to show a realistic operator control panel monitoring reaction parameters and valve controller positions.
“This is a complete virtual network, so you can set up your own entry detection rules and play on the defensive side to see whether or not your defenses are detecting the attacks,” said David Formby, a Georgia Tech postdoctoral researcher who has launched Fortiphyd Logic with Beyah to develop industrial control security products. “We provide access to simulated physical systems that allow students and operators to repeatedly study different parameters and scenarios.”
GRFICS is currently available as an open source, free download for use by classes or individuals. It runs on a laptop, but because of heavy use of graphics, requires considerable processing power and memory. An online version is planned, and future versions will simulate the electric power grid, water and wastewater treatment facilities, manufacturing facilities and other users of PLCs.
Formby hopes GRFICS will expand the number of people who have experience with the security of industrial control systems.
“We want to open this space up to more people,” he said. “It’s very difficult now to find people who have the right experience. We haven’t seen many attacks on these systems yet, but that’s not because they are secure. The barrier for people who want to work in the cyber-physical security space is high right now, and we want to lower that.”
Beyah and Formby have been working for several years to increase awareness of the vulnerabilities inherent in industrial control systems. While the community still has more to do, Beyah is encouraged.
“Several years ago, we talked to a lot of process control engineers as part of the NSF’s I-Corps program,” he said. “It was clear that for many of these folks then, security was not a major concern. But we’ve seen changes, and lots of people are now taking system security seriously.”













