
by Gary Mintchell | Aug 30, 2018 | Technology
Peter Diamandis, entrepreneur and founder of Singularity University and XPRIZE among many other things, interviewed his friend Ray Kurzweil at the Googleplex for a 90-minute (live) webinar on disruptive and dangerous ideas.

Diamandis promotes what he calls Abundance Thinking. He says, “By consuming and considering a steady diet of ‘crazy ideas,’ you train yourself to think bigger and bolder… a critical requirement for making impact. As humans, we are linear and scarcity-minded. As entrepreneurs, we must think exponentially and abundantly. At the end of the day, the formula for a true breakthrough is equal to ‘having a crazy idea’ you believe in, plus the passion to pursue that idea against all naysayers and obstacles.”
Kurzweil is Co-founder and Chancellor of Singularity University. He is also an XPRIZE Trustee, the Director of Engineering at Google, and “one of the best predictors of our exponential future.”
Diamandis and Kurzweil recorded a 90-minute conversation recorded on the YouTube video linked above. Here are 3 compelling ideas that came from the conversation as reported by Diamandis and sent in his newsletter. If you haven’t run across him, I recommend subscribing and having your mind blown.
The Nation-State Will Soon Be Irrelevant
Historically, we humans don’t like change. We like waking up in the morning and knowing that that the world is the same as the night before.
That’s one reason why government institutions exist: to stabilize society.
But how will this change in 20 or 30 years? What role will stabilizing institutions play in a world of continuous, accelerating change?
“Institutions stick around, but they change their role in our lives,” Ray explained. “They already have. The nation-state is not as profound as it was. Religion used to direct every aspect of your life, minute to minute. It’s still important in some ways, but it’s much less important, much less pervasive. [It] plays a much smaller role in most people’s lives than it did, and the same is true for governments.”
Ray continues: “We are fantastically interconnected already. Nation-states are not islands anymore. So we’re already much more of a global community. The generation growing up today really feels like world citizens much more than ever before, because they’re talking to people all over the world and it’s not a novelty.”
(Diamandis) previously shared (his) belief that national borders have become extremely porous, with ideas, people, capital and technology rapidly flowing between nations. In decades past, your cultural identity was tied to your birthplace. In the decades ahead, your identify is more a function of many other external factors. If you love space, you’ll be connected with fellow space-cadets around the globe more than you’ll be tied to someone born next door.
We’ll hit longevity escape velocity before we realize we’ve hit it
Ray and I share a passion for extending the healthy human lifespan.
I frequently discuss Ray’s concept of “longevity escape velocity” — the point at which, for every year that you’re alive, science is able to extend your life for more than a year.
Scientists are continually extending the human lifespan, helping us cure heart disease, cancer, and eventually neurodegenerative disease. This will keep accelerating as technology improves.
During my discussion with Ray, I asked him when he expects we’ll reach “escape velocity…”
His answer? “I predict it’s likely just another 10 to 12 years before the general public will hit longevity escape velocity.”
“At that point, biotechnology is going to have taken over medicine,” Ray added. “The next decade is going to be a profound revolution.”
From there, Ray predicts that nanorobots will “basically finish the job of the immune system,” with the ability to seek and destroy cancerous cells and repair damaged organs.
As we head into this sci-fi-like future, your most important job for the next 15 years is to stay alive. “Wear your seatbelt until we get the self-driving cars going,” Ray jokes.
The implications to society will be profound. While the scarcity-minded in government will react saying, “Social Security will be destroyed,” the more abundance-minded will realize that extending a person’s productive earning lifespace from 65 to 75 or 85 years old would be a massive boom to the GDP.
Technology will help us define and actualize human freedoms
The third dangerous idea from my conversation with Ray is about how technology will enhance our humanity, not detract from it.
You may have heard critics complain that technology is making us less human, and increasingly disconnected.
Ray and I share a slightly different viewpoint: that technology enables us to tap into the very essence of what it means to be human.
“I don’t think humans even have to be biological,” explained Ray. “I think humans are the species that changes who we are.”
Ray argues that this began when humans developed the earliest technologies — fire and stone tools. These tools gave people new capabilities, and became extensions of our physical bodies.
At its base level, technology is the means by which we change our environment, and change ourselves. This will continue, even as the technologies themselves evolve.
“People say, ‘Well, do I really want to become part machine?’ You’re not even going to notice it,” says Ray, “because it’s going to be a sensible thing to do at each point.”
Today, we take medicine to fight disease and maintain good health, and would likely consider it irresponsible if someone refused to take a proven, life-saving medicine.
In the future, this will still happen — except the medicine might have nanobots that can target disease, or will also improve your memory so you can recall things more easily.
And because this new medicine works so well for so many, public perception will change. Eventually, it will become the norm… as ubiquitous as penicillin and ibuprofen are today.
In this way, ingesting nanorobots, uploading your brain to the cloud, and using devices like smart contact lenses can help humans become, well, better at being human.
Ray sums it up: “We are the species that changes who we are to become smarter and more profound, more beautiful, more creative, more musical, funnier, sexier.”
My Take
I began studying international relations 50 years ago under an interesting professor. He was well up the chain at the CIA, Colonel in US Army Intelligence, PhD from Georgetown. Also, he was sort of a rebel. He took a liking to a somewhat rebellious kid from the farmlands.
It’s evident that the nation-state is in its death-throes. Trump and Xi and Putin are all trying to find ways to reassert power over a society and businesses that are increasingly global. Yes, there are emotional loyalties. But take a big step back and look at the sweep of history of the past 150 years. Think about what you see.
Technology throughout the entire history of humans has been both good and bad. But overall, it has benefitted humans. We eat better (well within our power of choice—don’t choose Doritos), live longer, have better housing and clothing, travel faster. We also have machines to help with backbreaking and dangerous labor.
As Diamandis says, think abundance rather than scarcity.

by Gary Mintchell | Aug 29, 2018 | Internet of Things, Standards
Industrial Networking Enabling IIoT Communication white paper
Working consortia of companies and individuals researching a technology provide great guidance for users of the technology—usually in the form of white papers. The Industrial Internet Consortium (IIC) has been especially prolific lately. This means many companies and individuals see the importance of donating time and expertise to the cause.
The IIC has announced the IIC Industrial Networking Enabling IIoT Communication white paper. The paper serves as an introductory guide on industrial networking for IIoT system designers and network engineers, and offers practical solutions based on key usage scenarios.
“Industrial networking is the foundation of IIoT,” said David Zhe Lou, Chief Researcher, Huawei Technologies. “There are many choices of networking technologies depending on the application, the industrial network, deployment situation and conditions, but there is no universal or preferred industrial networking solution.”
Industrial networking infrastructure and technologies reside at the IP layer and below, and enable industrial assets, such as machines, sites and environments, to connect to the business professionals supporting applications across a wide range of industry sectors. Industrial networking technologies provide the foundation for applications that enable manufacturing productivity and profitability.
“IIoT applications have different needs depending on the industrial application and therefore demand robust, flexible and secure networks,” said Cliff Whitehead, Business Development Manager, Rockwell Automation. “This white paper will help IIoT system designers and network engineers understand the tradeoffs they can consider when designing an industrial network architecture that will be a strong foundation for current and future IIoT scenarios.”
Industrial networking is different from networking for the enterprise or networking for consumers. For example, IIoT system designers and network engineers need to make decisions about using wired or wireless communications. They have to figure out how to support mobility applications such as vehicles, equipment, robots and workers. They must also consider the lifecycle of deployments, physical conditions, such as those found in mining and agriculture, and technical requirements, which can vary from relaxed to highly demanding.
“Networking technologies range from industry-specific to universal, such as the emerging 5G, which meets diverse industrial needs,” continued Jan Höller, Research Fellow at Ericsson. “Industrial developers need guidance when devising solutions to select the right networking technologies, and this white paper is the first step to providing the missing methods and tools.”
The Industrial Networking Enabling IIoT Communication white paper sets the stage for the Industrial Internet Network Framework (IINF), which will complement the Industrial Internet Connectivity Framework (IICF) by detailing requirements and best available technologies for the lower three layers of the industrial internet communication stack.
The full IIC Industrial Networking Enabling IIoT Communication white paper and a list of IIC members who contributed can be found on the IIC website:
The Industrial Internet Consortium is a program of the Object Management Group (OMG).

by Gary Mintchell | Aug 28, 2018 | Automation, Internet of Things, Manufacturing IT, Operations Management, Technology
Dell’s Edge and IoT Solutions bring new live to streaming video applications. Dell also expands portfolio of VMware solutions.
VMWorld presented by VMWare brought a crowd to Las Vegas this week—but not me. I know of bunch of Dell people there, but I’m not tapped in to VMWare. Know the company, though, and important technology for IT.
Last week Dell held a virtual conference for analysts and bloggers previewing some of the announcements that would be coming from the event.
This one reminds me of the history of video surveillance technology I’ve followed for at least 10 years. Maybe more. As I listened to the presentations, I thought about how all this IoT stuff we hear about is actually a confluence of technologies enabling realization of many dreams.
Dell Technologies’ Edge and IoT Solutions Division announced solutions and bundles to simplify deployment of secure, scalable solutions for edge computing and IoT use cases. This will drive workloads for computer vision – enabled by imaging sensors – and machine intelligence – characterized by structured telemetry from sensors and control systems. Dell Technologies has collaborated with Intel, who has helped advance these solutions with their computer vision and analytics technologies.
Cameras provide rich information about the physical world, but the deluge of video data creates too much data for humans to cost-effectively monitor for real-time decision making. Applying analytics, such as Artificial Intelligence, to these data streams automates powerful, actionable insights. Events driven by computer vision and analyzed together with telemetry from machines – including data that imaging sensors cannot provide, such as voltage, current and pressure – results in even more powerful insights.
By enabling computer vision with Dell Technologies IoT solutions, customers can more accurately, efficiently and effectively “see” relevant information pertaining to areas such as public safety, customer experience, and product inventory and quality. Surveillance is the first use case to which Dell Technologies has applied computer vision, so customers can more cost-effectively monitor events in the physical world and automate decision‐making.
The IoT Solution for Surveillance is specifically built to transform and simplify how surveillance technology is delivered with an easy to deploy and manage hyper-converged, software-defined solution. Available later this year to purchase as a package, the engineered, pre-integrated solution will provide a consistent foundation from edge to distributed core to cloud. It will also be ready to run on day one with customer data to speed the return on investment. The solution is currently available as a reference architecture to align systems and build a framework for computer vision learning and adoption for other use cases.
Dell Technologies IoT Solutions Partner Program
Through this program, Dell Technologies has identified several partners demonstrating strong use case focus and clear return on investment to create the new Dell Technologies IoT Connected Bundles. The bundles include sensors and licensed software from partners tailored for specific customer use cases, together with various combinations of Dell Technologies infrastructure spanning edge gateway, embedded PC and server hardware. This is in addition to complimentary software like VMware Pulse IoT Center for securing, managing and monitoring these solutions at scale.
Dell Technologies continues its commitment to openness and standardization in IoT. It actively participates in EdgeX Foundry, a vendor-neutral open source project focusing on building a common interoperability framework to facilitate an ecosystem for edge computing. The project, which has grown to more than 60 member organizations, recently announced the ‘California’ code release, a major step in evolving the EdgeX framework to support developer requirements for deployment in business-critical IoT applications. Dell Technologies Capital recently invested in IOTech Systems, a startup offering a commercially packaged version of this framework that enables customers to focus on their preferred value-add instead of supporting the open source code.
Dell Technologies also participates in the Industrial Internet Consortium (IIC), the OpenFog Consortium and the Automotive Edge Computing Consortium (AECC).
Other VMWorld News
At many companies, the time it takes for a product or service to go from concept to general availability depends on where a company is on its IT transformation journey. A more responsive IT department allows the business to respond more quickly to evolving external customer demands.
The benefits of the enhancements to Dell’s portfolio of VMware-based solutions include:
At the Edge:
- A ready-to-work experience enabling employees to boot up, log in, and be productive in minutes. Preconfigured apps and settings reduce time and resources associated with manual device imaging, repackaging and shipment. The Dell Provisioning for VMware Workspace ONE service enables automatic device setup and extends the efficiencies of cloud management to configuration and deployment.
- Simplified PC lifecycle management with expanded Dell PC-as-a-Service offerings for more customers and regions, including PCaaS for Business (20 to 300 units) and PCaaS for Enterprise (more than 300 units). Dell offers the latest PCs, deployment options – including Dell Provisioning for VMware Workspace ONE, software, peripherals, lifecycle services and financing – at a single, predictable price per seat per month.
- Scalability and stability with a consistent foundation from edge to distributed core to cloud with the new Dell IoT Solution for Surveillance, which automates scaling enterprises on day one with customer data, speeding up return on investment.
To the Core:
- Increase workload capacity, performance, scalability and control with the new Dell EMC VxRail G560, which delivers greater density in a 2U form factor. The Dell EMC VxRail G560 outperforms the previous Dell EMC VxRail G Series with 1.75X more cores; 2X increase in processing power; 4X more memory; and 3X capacity increase improvement in the boot device.
- Save time and lower operational expenses with synchronized Dell EMC VxRail Appliance and VMware vSAN update releases, so customers get the latest technology features as quickly as possible to rapidly address changing business needs.
- Continuous innovation and reduction of risk with Dell EMC VxRack SDDC engineered with Dell EMC VxRail E, P, V and now S Series models, all based on 14th generation PowerEdge servers.
- Faster time to production with the Dell EMC Networking Fabric Design Center, now including Dell EMC VxRail. The Fabric Design Center, an intuitive online tool, helps ensure the most efficient and effective networking design for deployment success.
- Investment protection with Dell EMC’s Future-Proof Loyalty Program protects customers’ core, edge and cloud investments, now including first-time HCI solution support with Dell EMC VxRail, for a set of advanced technology capabilities and programs that enable Dell EMC solutions to offer value for the entire lifetime of customers’ applications.
- Software-defined storage environment flexibility is further extended with Dell EMC vSAN Ready Nodes support on the new Dell EMC PowerEdge MX, which provides a highly flexible platform for vSAN Ready Nodes as HCI building blocks. The PowerEdge MX can hold up to eight vSAN Ready Nodes and help create a foundation for a self-sustained VMware Cloud Foundation cluster. It offers right-sized compute, storage and top-of-rack switching all in one high-density package, with the infrastructure managed through a single interface. The PowerEdge MX also supports SATA, SAS and NVMe storage devices, offering the cost benefits of storage tiering with VMware vSAN.

by Gary Mintchell | Aug 27, 2018 | Podcast
Podcast 178 What Problem Are You Solving
It has been said that computers are great at generating questions. They just can’t figure out the right question. Engineers are problem solvers. That is 99% of their education. Thing is—are they solving the right problem?
Businesses have adopted the open office architecture for many years. It solves a business cost problem—get more people per square foot. They publicly justify it, though, as solving the people collaboration problem. But they create a people productivity problem. The signal v noise blog from BaseCamp called Library Rules
[https://m.signalvnoise.com/library-rules-how-to-make-an-open-office-plan-work-f9f6d69a2d4c] proposes an interesting solution. The open office has existed for centuries. And it works fantastically. It’s called a library. Check out library rules for your open office dilemma.
My grandkids naturally collaborate on iPads with Minecraft.
Solving technology problems is a lot of fun for engineers. They look at everything as a technology problem. But then there are problems that are not technology. Such as people problems. Take a look at Facebook’s problems right now. They are not technology; they are ethical.
A generation of engineers have worked hard at solving process control problems. I reflect on a chat I had with Schneider Electric process automation leaders Gary Freburger and Peter Martin about solving business problems in addition to technology problems.

by Gary Mintchell | Aug 24, 2018 | Automation, Operator Interface, Technology, Workforce
Simulators are great training tools. It sure beats flying 777s around for your annual pilot recert. Gaming technology has become so good along with many other technologies, that operators of process plants and machinery should be well trained to respond appropriately to any emergency.
Georgia Institute of Technology sent this information about an advancement in simulation for operator training. Good stuff.
A simulator that comes complete with a virtual explosion could help the operators of chemical processing plants – and other industrial facilities – learn to detect attacks by hackers bent on causing mayhem. The simulator will also help students and researchers understand better the security issues of industrial control systems.
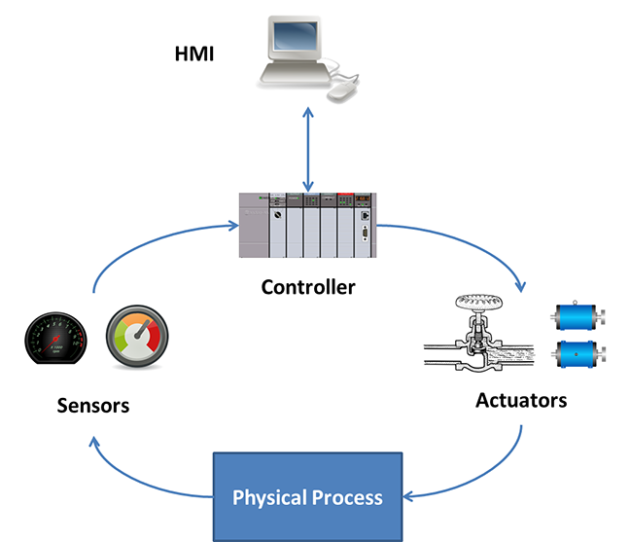
This flow chart shows data flows within a simulated chemical processing facility.
Facilities such as electric power networks, manufacturing operations and water purification plants are among the potential targets for malicious actors because they use programmable logic controllers (PLCs) to open and close valves, redirect electricity flows and manage large pieces of machinery. Efforts are underway to secure these facilities, and helping operators become more skilled at detecting potential attacks is a key part of improving security.
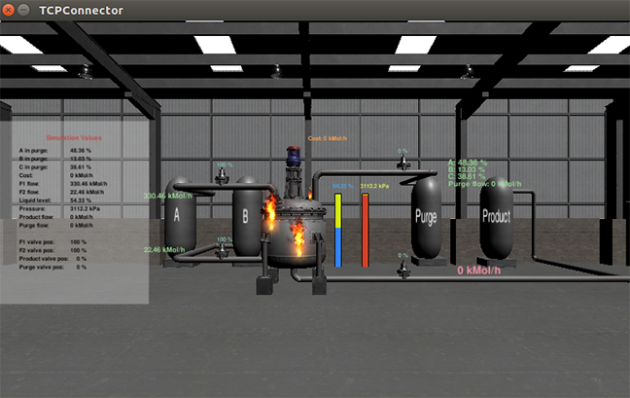
Screen captures show a simulated explosion in a chemical processing plant precipitated by a cyberattack on the system.
“The goal is to give operators, researchers and students experience with attacking systems, detecting attacks and also seeing the consequences of manipulating the physical processes in these systems,” said Raheem Beyah, the Motorola Foundation Professor in the School of Electrical and Computer Engineering at the Georgia Institute of Technology. “This system allows operators to learn what kinds of things will happen. Our goal is to make sure the good guys get this experience so they can respond appropriately.”
Details of the simulator were presented August 8 at Black Hat USA 2018, and August 13 at the 2018 USENIX Workshop on Advances in Security Education. The simulator was developed in part by Atlanta security startup company Fortiphyd Logic, and supported by the Georgia Research Alliance.
The simulated chemical processing plant, known as the Graphical Realism Framework for Industrial Control Simulations (GRFICS), allows users to play the roles of both attackers and defenders – with separate views provided. The attackers might take control of valves in the plant to build up pressure in a reaction vessel to cause an explosion. The defenders have to watch for signs of attack and make sure security systems remain operational.
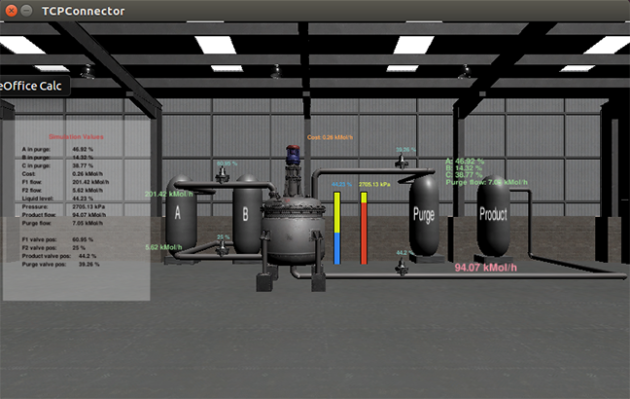
Screen capture shows a chemical processing plant in which critical parameters are rising due to false process data and control commands injected by an attacker.
Of great concern is the “man-in-the-middle” attack in which a bad actor breaks into the facility’s control system – and also takes control of the sensors and instruments that provide feedback to the operators. By gaining control of sensors and valve position indicators, the attacker could send false readings that would reassure the operators – while the damage proceeded.
“The pressure and reactant levels could be made to seem normal to the operators, while the pressure is building toward a dangerous point,” Beyah said. Though the readings may appear normal, however, a knowledgeable operator might still detect clues that the system has been attacked. “The more the operators know the process, the harder it will be to fool them,” he said.
The GRFICS system was built using an existing chemical processing plant simulator, as well as a 3D video gaming engine running on Linux virtual machines. At its heart is the software that runs PLCs, which can be changed out to represent different types of controllers appropriate to a range of facilities. The human-machine interface can also be altered as needed to show a realistic operator control panel monitoring reaction parameters and valve controller positions.
“This is a complete virtual network, so you can set up your own entry detection rules and play on the defensive side to see whether or not your defenses are detecting the attacks,” said David Formby, a Georgia Tech postdoctoral researcher who has launched Fortiphyd Logic with Beyah to develop industrial control security products. “We provide access to simulated physical systems that allow students and operators to repeatedly study different parameters and scenarios.”
GRFICS is currently available as an open source, free download for use by classes or individuals. It runs on a laptop, but because of heavy use of graphics, requires considerable processing power and memory. An online version is planned, and future versions will simulate the electric power grid, water and wastewater treatment facilities, manufacturing facilities and other users of PLCs.
Formby hopes GRFICS will expand the number of people who have experience with the security of industrial control systems.
“We want to open this space up to more people,” he said. “It’s very difficult now to find people who have the right experience. We haven’t seen many attacks on these systems yet, but that’s not because they are secure. The barrier for people who want to work in the cyber-physical security space is high right now, and we want to lower that.”
Beyah and Formby have been working for several years to increase awareness of the vulnerabilities inherent in industrial control systems. While the community still has more to do, Beyah is encouraged.
“Several years ago, we talked to a lot of process control engineers as part of the NSF’s I-Corps program,” he said. “It was clear that for many of these folks then, security was not a major concern. But we’ve seen changes, and lots of people are now taking system security seriously.”













